Unlike spam attacks, which work with very short life cycles for domains and links, established cloud services cannot simply be placed on a blocklist. It is therefore important to find a clear-cut separation for individual links within these services and to sort the links.
A phishing email with an alleged order confirmation and an HTML attachment. If a malware scanner jumps to “archive.org”, it is because of the obfuscation layer used.
The risk of HTML attachments
HTML attachments have been a major risk for companies for years. Double-clicking on the attachment opens it in the default browser. JavaScript or embedded IFrames are then executed directly and without further enquiry. In the case of Office documents with macro functionality, there was still a query to the user, or it was possible to restrict execution throughout the entire company via group policy. In the browser, such security measures are completely absent or would restrict the functionalities of the modern Internet too much. See also: HTML attachments: the underestimated danger.
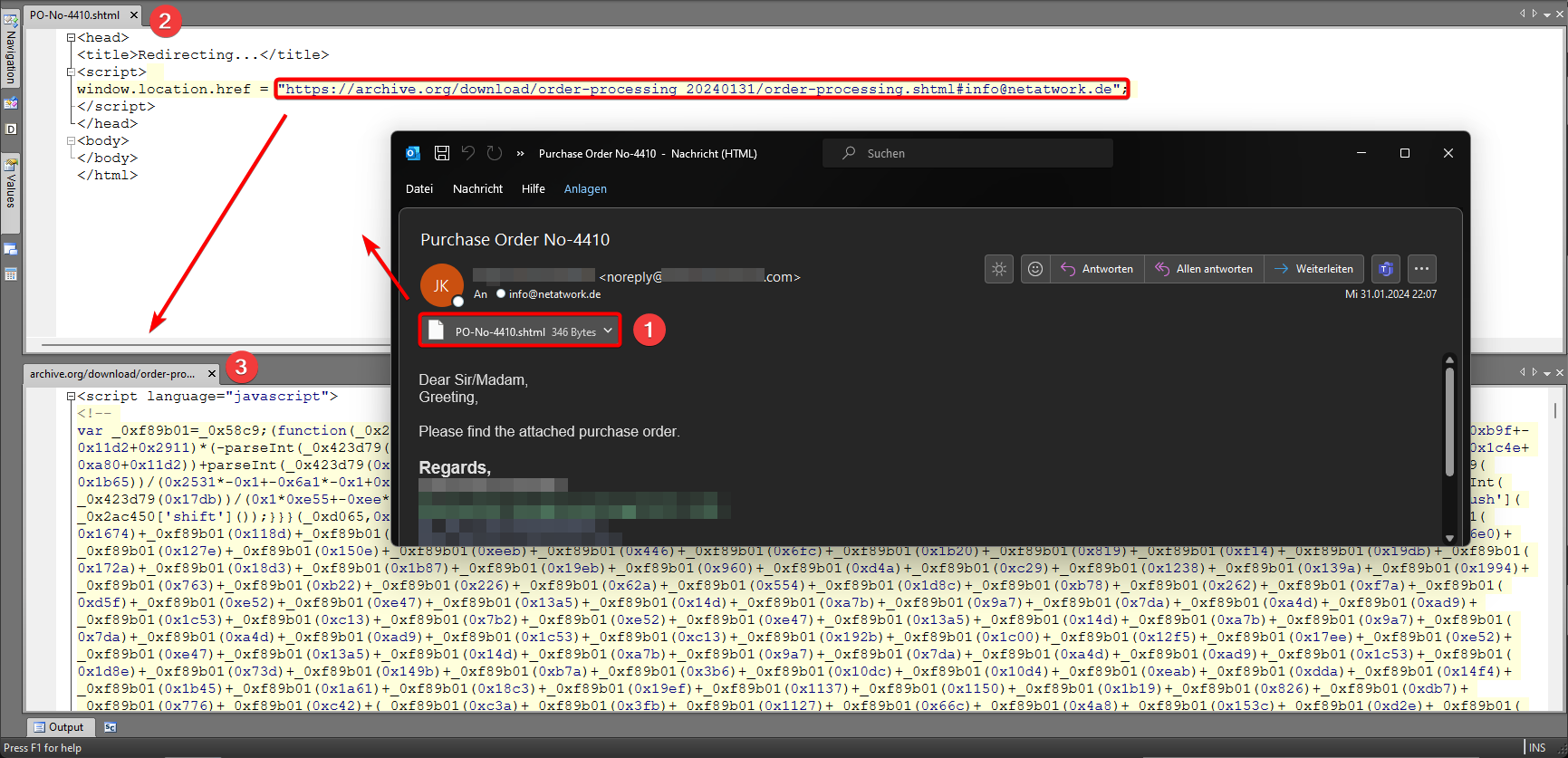
In our example, double-clicking on the alleged invoice opens the attachment, and a simple JavaScript redirect to archive.org, the so-called Internet Archive and best known for its Wayback Machine, can be recognised. What is less well known is that users can upload all kinds of content there so that it is preserved for eternity in the Internet archive. This then attracts spammers who abuse this service for their own purposes.
NoSpamProxy also detects malicious URLs in attachments
In addition to the use of short URLs in emails, which hide the actual malicious URL within the email behind a service such as “bit.ly”, another trend in recent years is that the URLs of the email are also “moved” to the attachments. In our example, the URL that leads to the phishing website archive.org is no longer in the email body, but can be found in the email attachment. This makes it easier for spammers to conceal their activities.
However, NoSpamProxy can also analyse HTML attachments and reports URLs contained in such attachments to 32Guards. Accordingly, it is initially not a problem if the URL can be found in the attachment. Other mail security solutions that do not look so deeply into file formats often do not see the link at all, and the spammers would have achieved their goal.
Phishing thrives on social engineering
The presence of an attachment is therefore another indicator of malicious emails. However, since in our example the HTML attachment contains the recipient email address as part of the URL (see screenshot), each HTML attachment will have a different hash value. This means that the comparison with known hash values of malicious documents is ineffective here.
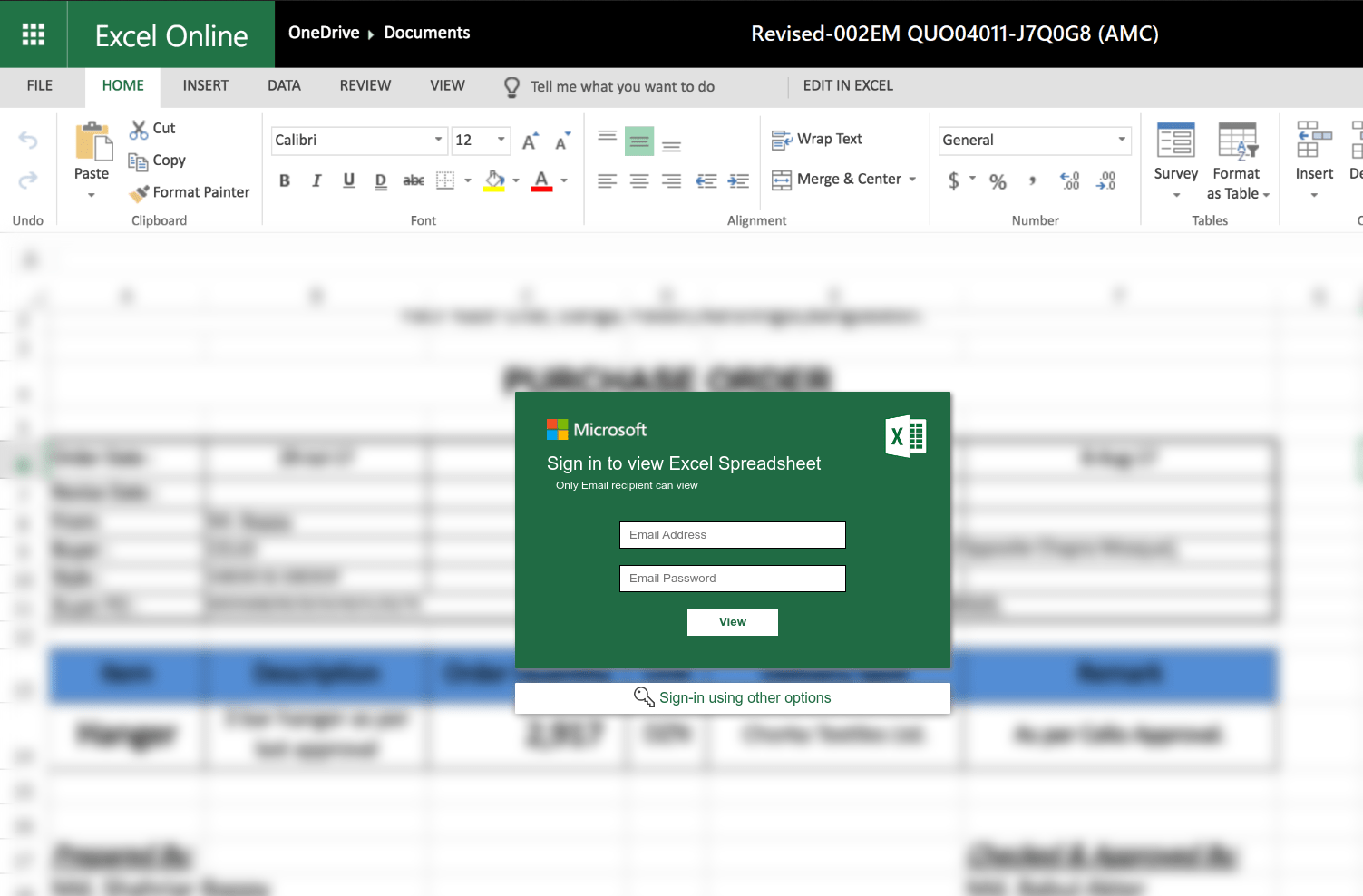
If you statically analyse the content behind the link to “archive.org” from the HTML attachment, you will discover a “JavaScript obfuscation layer”. If you run the content in the browser and render it, a very elaborately designed, supposed Excel application appears. This asks for a user name and password, the entry of which is supposed to make it possible to view the invoice (which can already be surmised in the background). This also shows that phishing always relies heavily on a social engineering component and that attackers often put a lot of energy into their work.
The obfuscated JavaScript code conceals a very elaborately designed, fake Excel application.
Cloud services as an attack vector
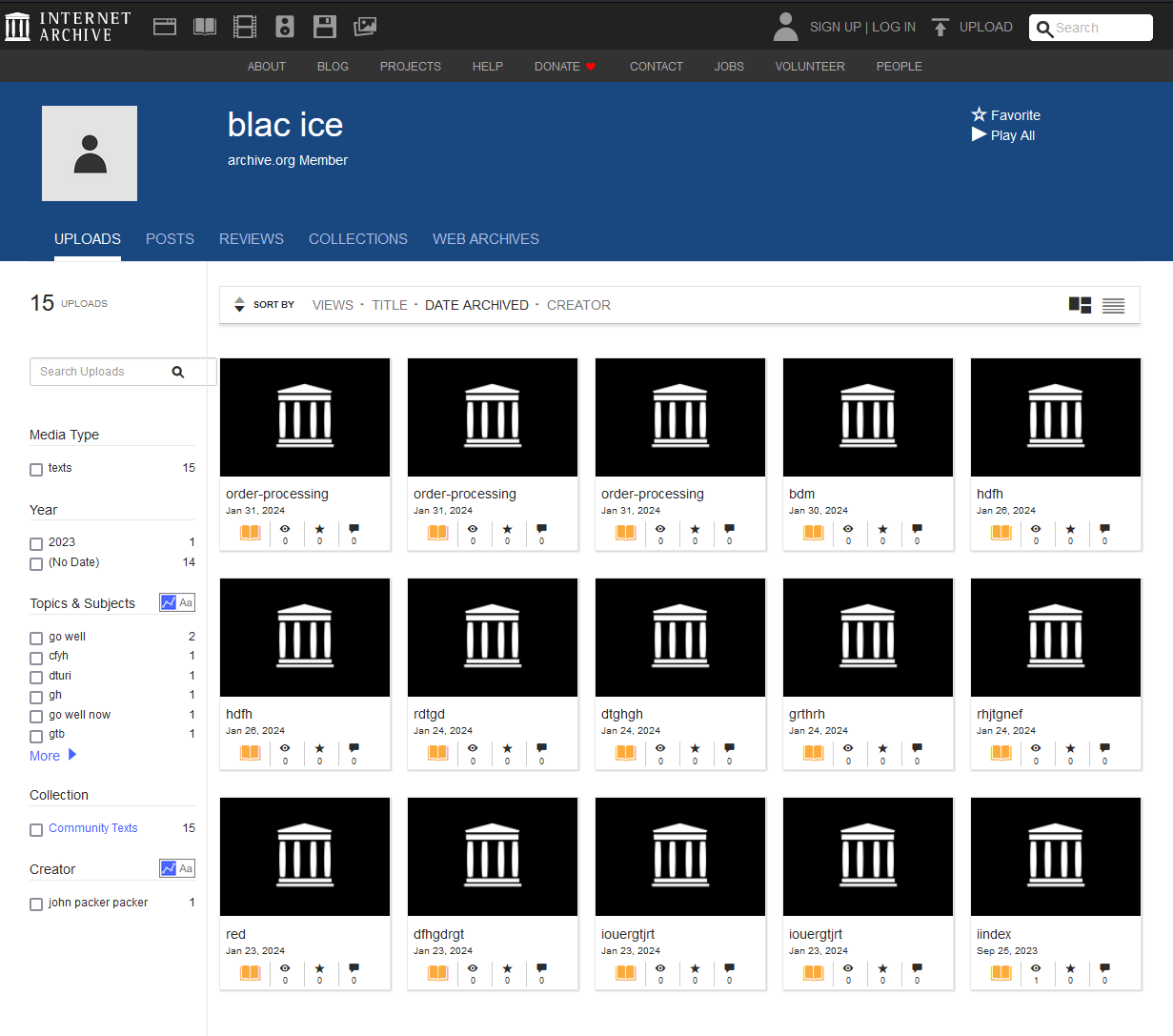
Cloud services are being used more and more frequently, and we have reported elsewhere on the misuse of Microsoft’s OneDrive cloud service to distribute Qakbot, for example. However, the reporting mechanisms for cloud services generally work well, for example the corresponding reporting page on archive.org. Reported content is then promptly removed again. Spammers therefore only ever have a short window of time to collect the login data, as in our example. The content of the user concerned has now been deleted from archive.org. Often, however, a new profile is quickly created and other phishing websites are uploaded under a new name.
If you look at the user’s profile page on “archive.org”, you quickly realise that other phishing pages have been uploaded there as well.
32Guards blocks threats
Within NoSpamProxy, 32Guards is a filter that influences the calculation of the Spam Confidence Level (SCL) on the one hand, and an action that can directly reject threats temporarily or permanently on the other. The evaluation of emails by 32Guards is based on the analysis of a series of indicators in the form of metadata, which are extracted from the email by NoSpamProxy and sent to 32Guards, where they are analysed accordingly. This evaluation results in a final assessment of the email. The exact details can be viewed in a separate “32Guards” activity in the respective message track of the corresponding email.
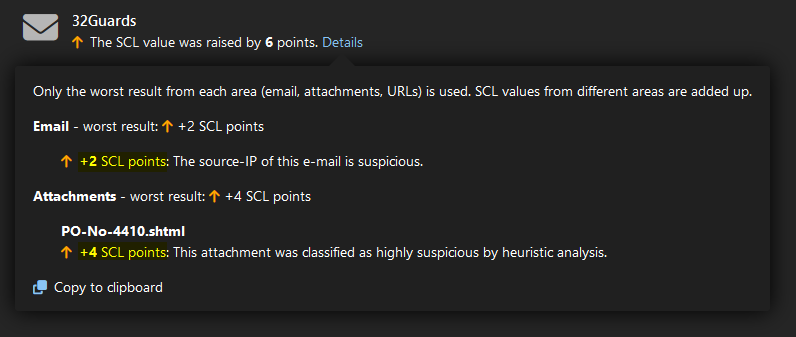
Three independent areas are used within the risk assessment. On the one hand, the email area, which also takes into account the reputation of the IP address of the sending email server, for example, the “URLs” area and the “Attachments” area. SCL points are only added from different areas and the highest score is taken into account in each case. In our example, the SCL value was increased by 6 points by 32Guards, split between the email area with 2 SCL points and the attachment area with 4 SCL points. The “real-time blocklists” used in NoSpamProxy had not yet taken effect in our example, but the IP address of the sending email server was already rated as suspicious by 32Guards at this point. However, the decisive factor was 32Guards’ heuristic evaluation of the HTML attachment in this email. With 6 SCL points, this was enough to successfully fend off this phishing email.
Further information
Not yet using the 32Guards Sandbox?
With NoSpamProxy and the 32Guards Sandbox, you can reliably protect your company from cyber attacks. Request your free trial version now!