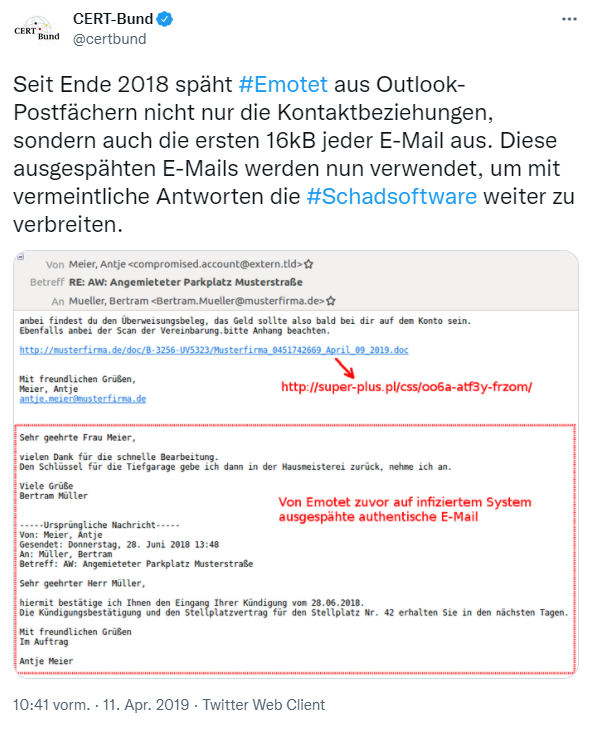
The Computer Emergency Response Team of the German Federal Administration (CERT-Federal for short) warned about the new attack vector in Emotet in April 2019.
Source: Twitter
While it was initially still possible to say that one of the communication partners must have been infected and the email must have leaked out via it, this is no longer necessarily the case today. In 2021, there were several zero-day security vulnerabilities for on-premises hosted Exchange servers, which theoretically could have leaked the entire email communication if the Exchange servers were not patched or not patched in time.
However, one should assume that email reply chain attacks are highly effective in their social engineering effect, since the fake reply to a real communication takes place and one usually knows the alleged communication partner very well. The fact that the fake email was not sent by the communication partner at all, but by unknown email servers under the control of the spammers, is usually not even recognizable for the layman. Often, laypersons cannot even imagine that it is at all possible for someone other than the communication partner to be able to access the previous email history.
QakBot with OneDrive Personal Links
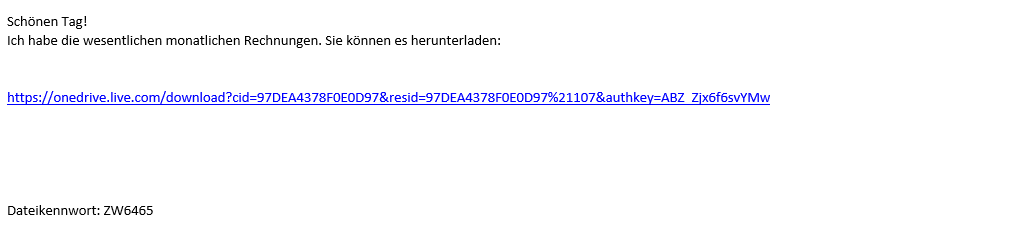
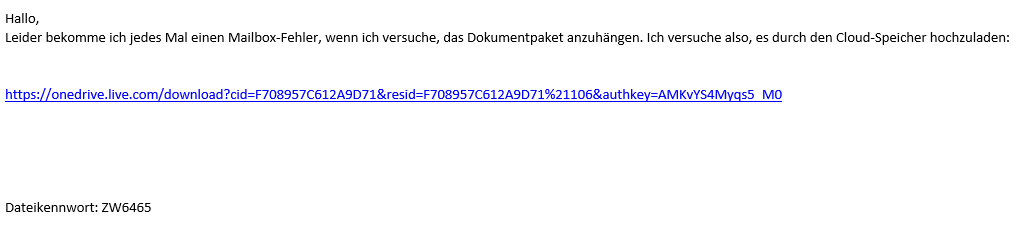
Another popular attack vector is the use of legitimate cloud services to spread malware. In the current QakBot waves, one approach is to resort to the email reply chain attacks described above, and the other is to include a link to Microsoft’s OneDrive personal cloud service in the fake reply, as exemplified in the following examples.
Fake replies from QakBot with links to “OneDrive Personal”. Note the “file password” at the end.
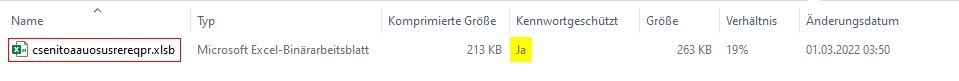
The link hides a password-protected zip archive.
A closer look reveals that the zip archive hides a binary Excel document with macro functionality, which successfully evades malware scanners due to password protection. The password required to decrypt the zip archive is included at the end of the fake response. This is probably also the reason why these links still work days after the spam wave and have not been blocked by Microsoft.
OneDrive? OneDrive Business? OneDrive Personal!
Regarding the link structure of OneDrive links, it quickly becomes apparent that there is a clear difference between “OneDrive Business” as well as “OneDrive Personal”. When I create a link to share, you immediately notice that “OneDrive Business” follows the pattern “-my.sharepoint.com“ or „.sharepoint.com”. This can be distinguished very well as a result. So let’s share a file via “OneDrive Personal” to see how these links look like.
A file shared via “OneDrive Personal”
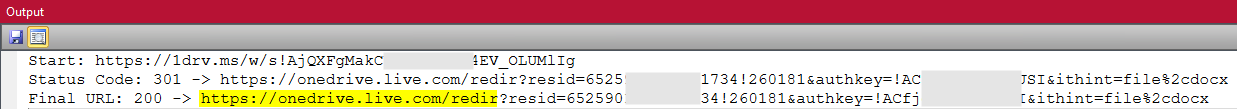
The first thing you notice is that the link, unlike the QakBot examples above does not point to “onedrive.live.com” at all, but to Microsoft’s URL shortener “1drv.ms“. Next, let’s see what the link behind it looks like.
Microsofts URL Shortener „1drv.ms“
So at first glance it looks like the QakBot links from above, right? At second glance you can see that the path doesn’t start with “onedrive.live.com/download” like QakBot, but with “onedrive.live.com/redir“.
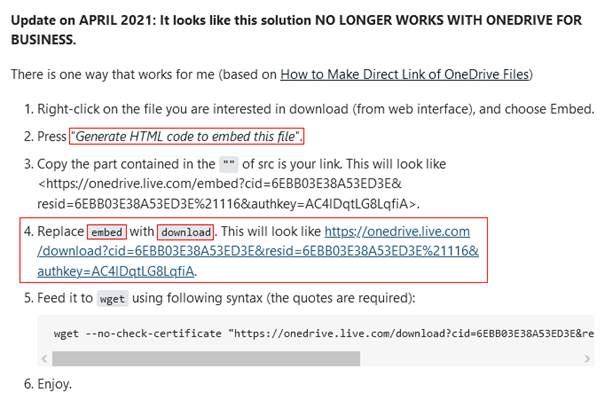
A “recipe” on StackExchange reveals how to create this type of “onedrive.live.com/download” links
It seems that these “OneDrive Personal” links should not be on the way by default, but that the path “onedrive.live.com/embed” has to be changed to “onedrive.live.com/download” first.
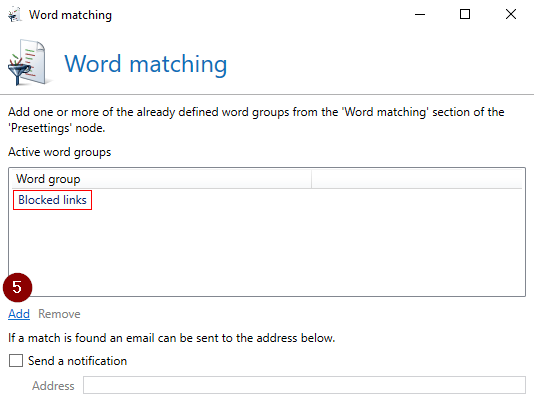
Protection against email reply chain attacks: Word match filter for blocking unwanted links.
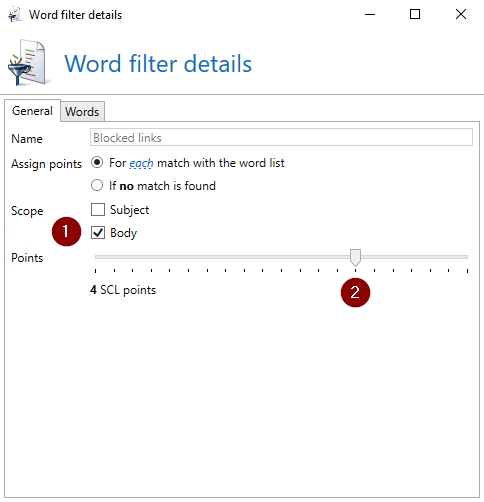
With the word match filter you can assign SCL points to unwanted links in NoSpamProxy.
Under Configuration > Presettings, add a new word group to the word matches, restrict the range to the “email body” and assign 4 SCL or more.
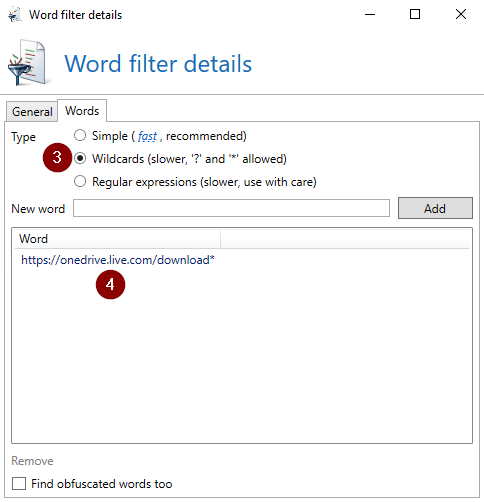
As type use “Placeholder” and enter “https://onedrive.live.com/download*” (with a “*” at the end).
In all inbound rules it is necessary to include – if not already present – the “Word matches” filter and add the newly created “Blocked links” word group.
Since “word matches” is a filter, in the event that such a link should be in use at a certain partner after all and an exception should now be defined, the Level of Trust system comes in handy in these cases, because trusted email can overrule a filter accordingly.
With this knowledge you have the possibility to handle such links to “OneDrive Personal” in NoSpamProxy more strictly. Ideally, one has the function “URL Safeguard” with the option “URL Tracking” already in use. Then you can conveniently filter for all emails with the domain “onedrive.live.com” in the message tracking and make the decision for the company whether you want to filter here more strictly in the future in terms of IT security.
You want to protect yourself from email reply chain attacks and don’t have NoSpamProxy in use yet?
With NoSpamProxy you can reliably protect your company against cyber attacks. Request your free trial version now!