Emotet is history but the attack mechanisms remain
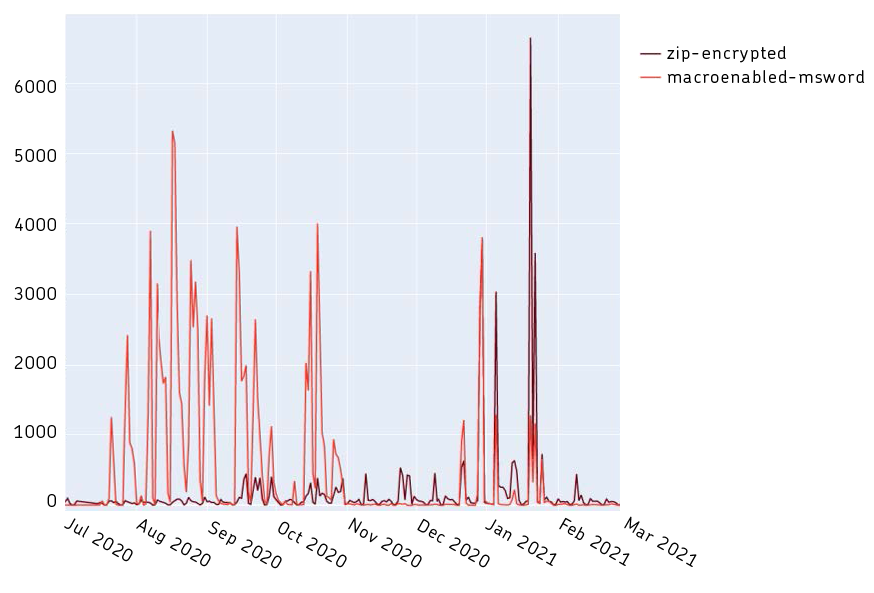
Situation and assessment: After international cooperation among security authorities led to a takedown of the Emotet botnet in January, the threat situation has changed drastically. One of the largest sources of malware has dried up. So far, no comparable successor has emerged and the situation is thus much more diffuse. From our point of view, it was interesting how flexibly Emotet had adapted its strategy in the last weeks before shutting down: from Word files with malicious macros, Emotet switched to encrypted archive attachments.
The figure shows the number of observed attachments of incoming emails of the respective type. In the summer, the classic Emotet strategy (light line), which relied on Word files with macros, still dominated. The clear peaks show the different attack waves. Outside of the attack waves, the sightings of these file formats are very low. Towards the end of 2020, the change in strategy towards encrypted archives can be clearly seen (dark line). After the takedown in January, the sightings have almost completely decreased.
Our recommendation: Unfortunately, it must be assumed that the strategies used by Emotet will live on. These will certainly include the use of encrypted ZIP formats and the use of URL shorteners. For both attack vectors, we offer background information and tips on our website.
With our Metadata Service 32Guards, we can keep a close eye on what is happening and will point out any developments at an early stage. At the moment, there does not seem to be any large-scale use by attackers, but the encrypted archive formats in particular appear to have great malicious potential. Caution is still advised here, and we recommend avoiding them in legitimate email communication.
The second lesson learned is how flexibly even a large-scale malicious infrastructure like Emotet can change its attack patterns and thus react to defence mechanisms. The only defence is to react quickly and flexibly to new attack patterns. Manufacturers and customers of email security solutions must work together more closely to detect waves of attacks early on using data-driven analysis approaches and to initiate countermeasures together.
“Pill spam”, a familiar concept with an improved approach
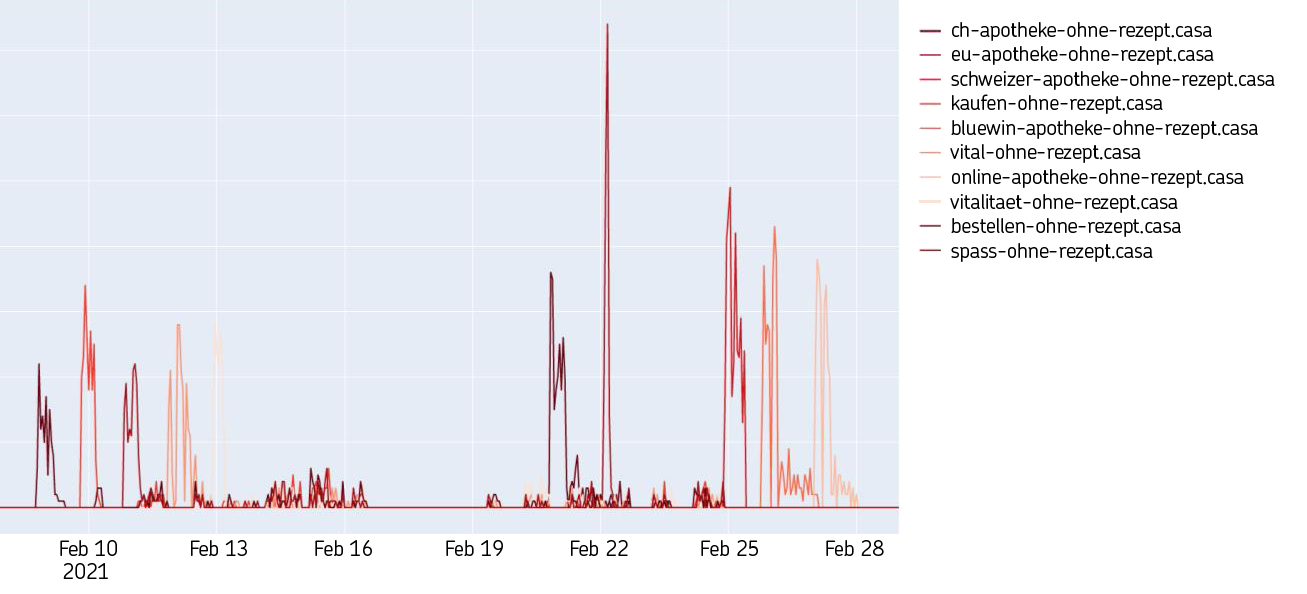
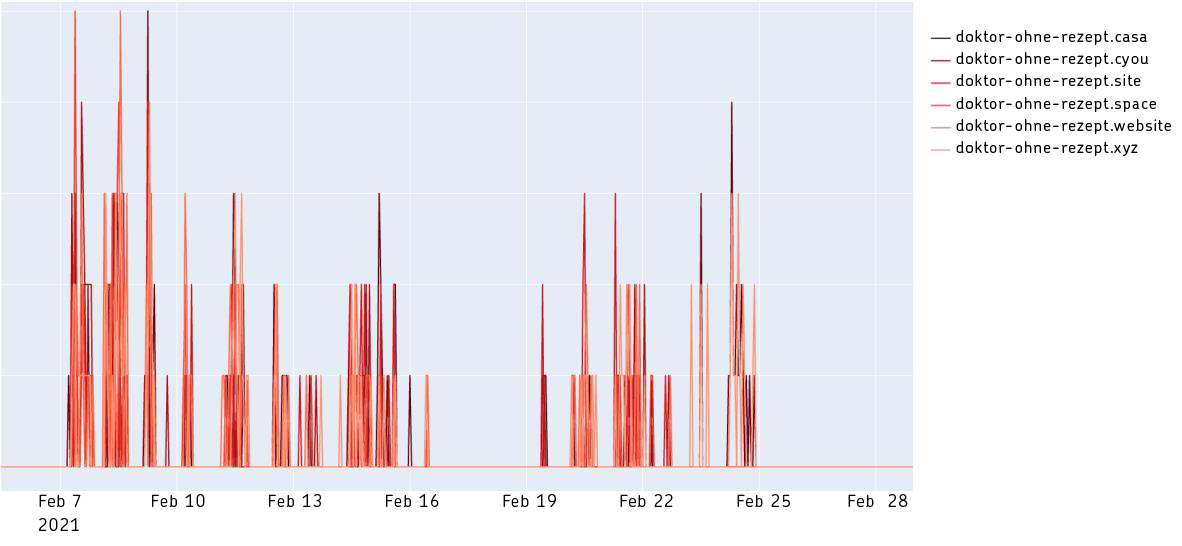
Situation and assessment: In the first quarter of 2021, we observed a significant increase in spam activity. Thematically, the campaigns with advertisements for relevant medicines were a familiar approach and technically, the emails were also rather simple – not to say poorly made. However, the structure of the attacks behind the spam email was noteworthy: a high number of domains were registered for the fake online shop behind the campaign. In the course of the attacks, these were quickly changed within one or a few days. Two extracts of these URLs are shown in the following graphics. The individual spam waves and the domains that were quickly changed are clearly visible.
The situation is not limited to the top-level domain “.casa”, as the second graphic shows.
Our recommendation: We repeatedly observe spam and malware attacks that work with very short life cycles for domains and links. This method makes it difficult for classic mechanisms to reliably detect these waves. In order to be able to react to such attacks, the email security component must be updated within a very short time. Ideally, such a component is connected to a corresponding service which uses corresponding metrics in ad-hoc data analytics to detect such attacks at the very beginning and automatically alerts all connected instances.
Using Google links to disguise your own URL
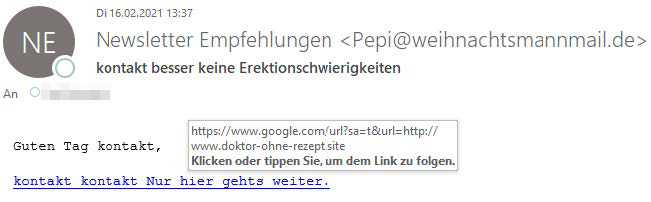
Situation and assessment: In the first quarter, we noticed that spammers are increasingly trying to disguise their own URL. One frequently used way is to embed the actual link in a Google link (see example). With this rather simple trick, many conventional URL reputation filters can be circumvented, as they often have the domain google.com on their whitelist.
Our recommendation: Administrators should check the email security solution they use for this aspect, but also the security infrastructure for protecting the actual web traffic. As a general rule, much more sophisticated mechanisms for reputation checks are now available, which deliver considerably better results even with multi-level approaches.
The latest approach: .cam domains for spam URLs
Situation and assessment: At the end of the first quarter, a new domain extension became popular among spammers with the domain .cam. The domain – originally intended for photography and film – is easily confused by the user with the widespread domain .com and is probably why it has recently become popular with spammers. In our monitoring, email traffic coming from this domain revealed itself almost exclusively as spam. The graph shows the significant increase in daily sightings on a moving average basis.
Our recommendation: For the evaluation of incoming emails, the domain ending .cam can be considered a good indication of spam and should be weighted accordingly. With modern, self-learning whitelisting methods such as the Level of Trust from NoSpamProxy, any false positives can be avoided.