With the release of NoSpamProxy Server version 14.1 in August 2023 and the November 2023 update of NoSpamProxy Cloud, the 32Guards Sandbox is available to all customers as a paid service. So it’s time to take a closer look at the 32Guards Sandbox using an example.
What is a sandbox?
A sandbox is a complex system to which files are passed for inspection. Unlike a traditional virus scanner, it does not only check whether the file is already known as a virus or not. A sandbox executes the file and monitors it. This is called “detonating”.
For this purpose a virtual computer is installed and booted. Then the file to be scanned is copied to this virtual machine and detonated. Now the most important task of the sandbox begins: It must observe what happens in the computer. The sandbox can then draw conclusions about the malware content of the file from the observed behaviour.
How does the 32Guards sandbox work?
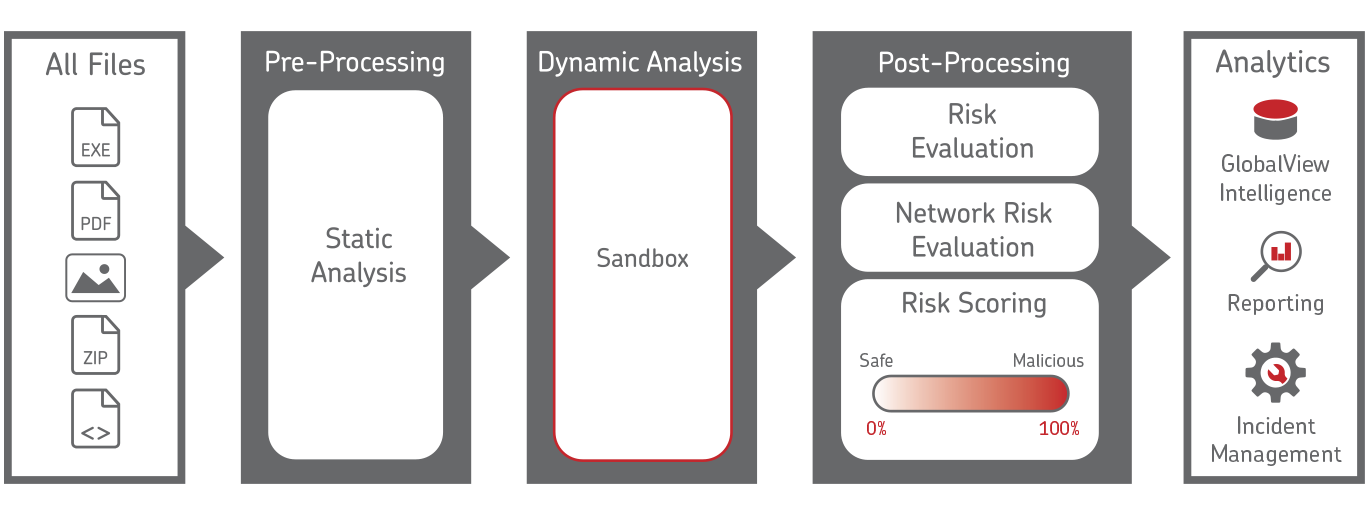
The 32Guards sandbox analyses files, URLs and command & control traffic. The latter describes the exchange of data between an infected computer and its “master” in the network, from whom it receives new commands.
Before a file is uploaded from NoSpamProxy to the sandbox, NoSpamProxy creates a hash value and asks the sandbox if it already knows the hash. If the hash is known, it is also queried whether the hash is good or bad. This is referred to as Level 1 (hash query) and Level 2 (file upload).
The files to be checked are transmitted and checked in encrypted form. To make the testing process as efficient as possible, an expected behavior is predicted based on the file type (static analysis) and an environment optimized for this prediction is run up (dynamic analysis). Only if the expected behavior does not occur will additional virtual machines be provisioned (post-processing).
As soon as a file or URL is recognised as bad, a fingerprint of the respective object is created.
Unwanted archives get support
The following example dates from January 2024 and is an email with the suspicious attachment “Quotation40059.r00”, i.e. a RAR archive. The “.r00” file extension is a relic from earlier times when “backup copies” had to be split across several floppy discs with a maximum storage capacity of 1.44 MB. This meant that you could later give your friends a “decentralised backup” in the form of a stack of floppy disks. “.r00” signalled the first part of the archive.
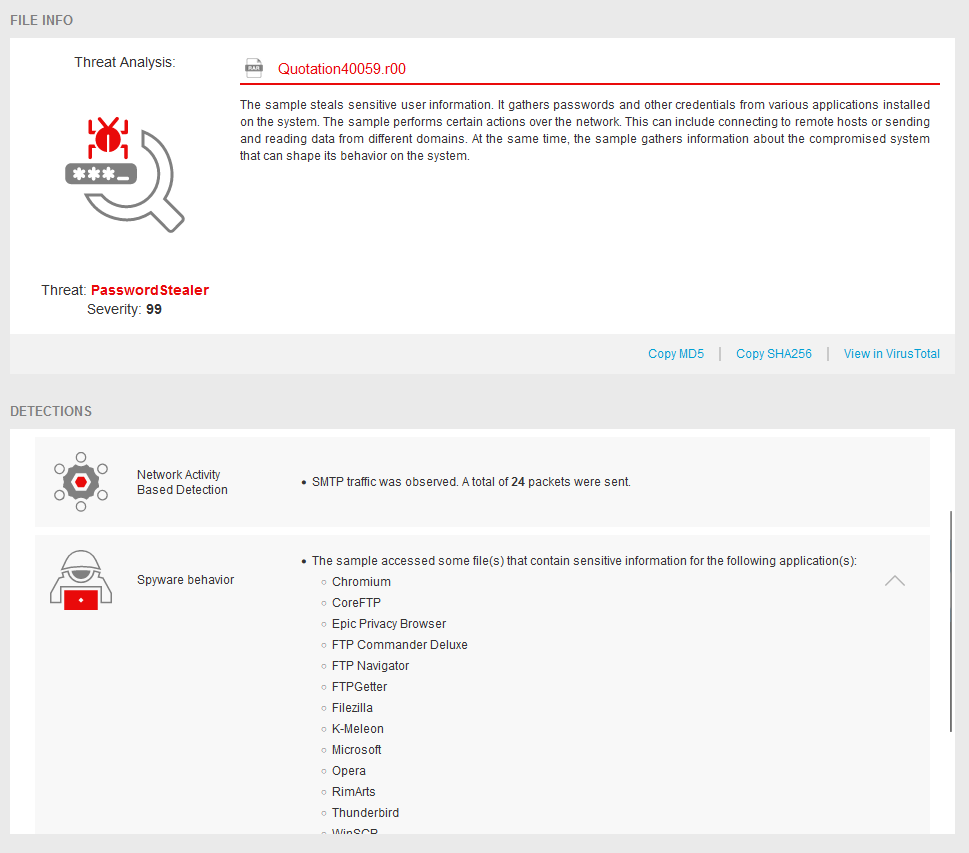
A 32Guards sandbox report with a detection of a PasswordStealer | Source
The built-in support for archives in Windows is rather rudimentary and often reaches its limits even with common ZIP archives.
As soon as a ZIP archive with password protection is not provided with the weak “ZipCrypto” method, but with AES-256 encryption, the user is faced with the problem that this archive cannot be unpacked with Windows 11 on-board tools.
The result: The company rolls out tools such as “7-Zip” or “WinRAR”, and at the same time, support for all the old formats such as “.ace”, “.arj” or even “.r00”, “.r01”, “.r02” etc. is brought into the house. Even if you don’t even have these file extensions on your screen the spammers know them all and use them because 7-Zip and other tools can open them without any problems.
Insert archives, extract passwords
The first screenshot shows the summary of the 32Guards sandbox report for the RAR archive. The analysis in the sandbox has detected a “password stealer”, as passwords of the various installed programmes were queried by the malware in the prepared environment of the 32Guards sandbox.
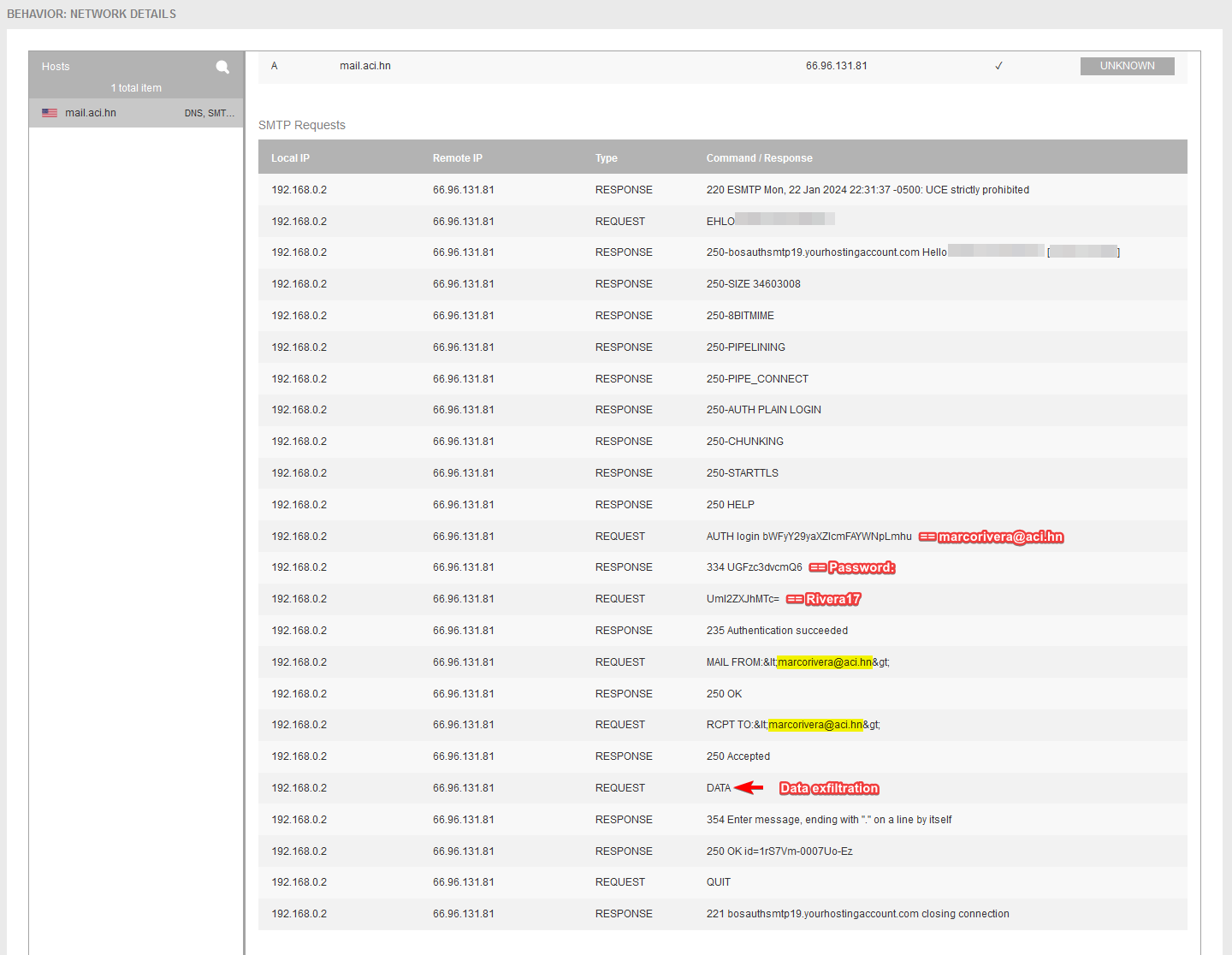
Here you can see the outbound SMTP communication via port 587 with the email server “mail.aci.hn” and the “Data Exfiltration.
.r00 wants to phone home
The malware also “phones home”, and contact is made with the criminals’ command-and-control server via outbound SMTP communication on port 587. Unfortunately, there are still many companies that allow outbound SMTP connections via port 25 or 587 outside of a legitimate email server or email server cluster.
If a company has already completely migrated to Microsoft 365, the question arises as to whether clients in the network need to communicate outbound via port 25 or 587 at all, or whether a more restrictive approach should be taken here. Not so fun fact: The malware family Agent Tesla can even send data via a Telegram channel in addition to the classic route via HTTP(S) or FTP.
What happens in the sandbox stays in the sandbox
In the second screenshot, you can also see that the malware performs a so-called SMTP-Auth authentication with the “Login” method after the SMTP connection has been established. The email address for the mailbox and the password are only encoded and transmitted using BASE64.
After authentication, it is apparent that the malware sends an email to the previously authenticated email address and enters itself as the sender and recipient. If server-side forwarding is also set up in the mailbox, the attacker can easily access the compromised passwords from another location.
You can imagine what would have happened if this RAR archive had not been executed in the controlled environment of the 32Guards sandbox, but in your own company: the leaked access data would have enabled full access to the corresponding accounts. Thanks to the 32Guards Sandbox, everything remains as it is and where it should be: in the sandbox.
Three questions for more security
Are RAR archives allowed as attachments in emails?
Are outbound SMTP connections blocked by the client in the firewall?
Has multi-factor authentication (MFA) been implemented for all user accounts in the company?
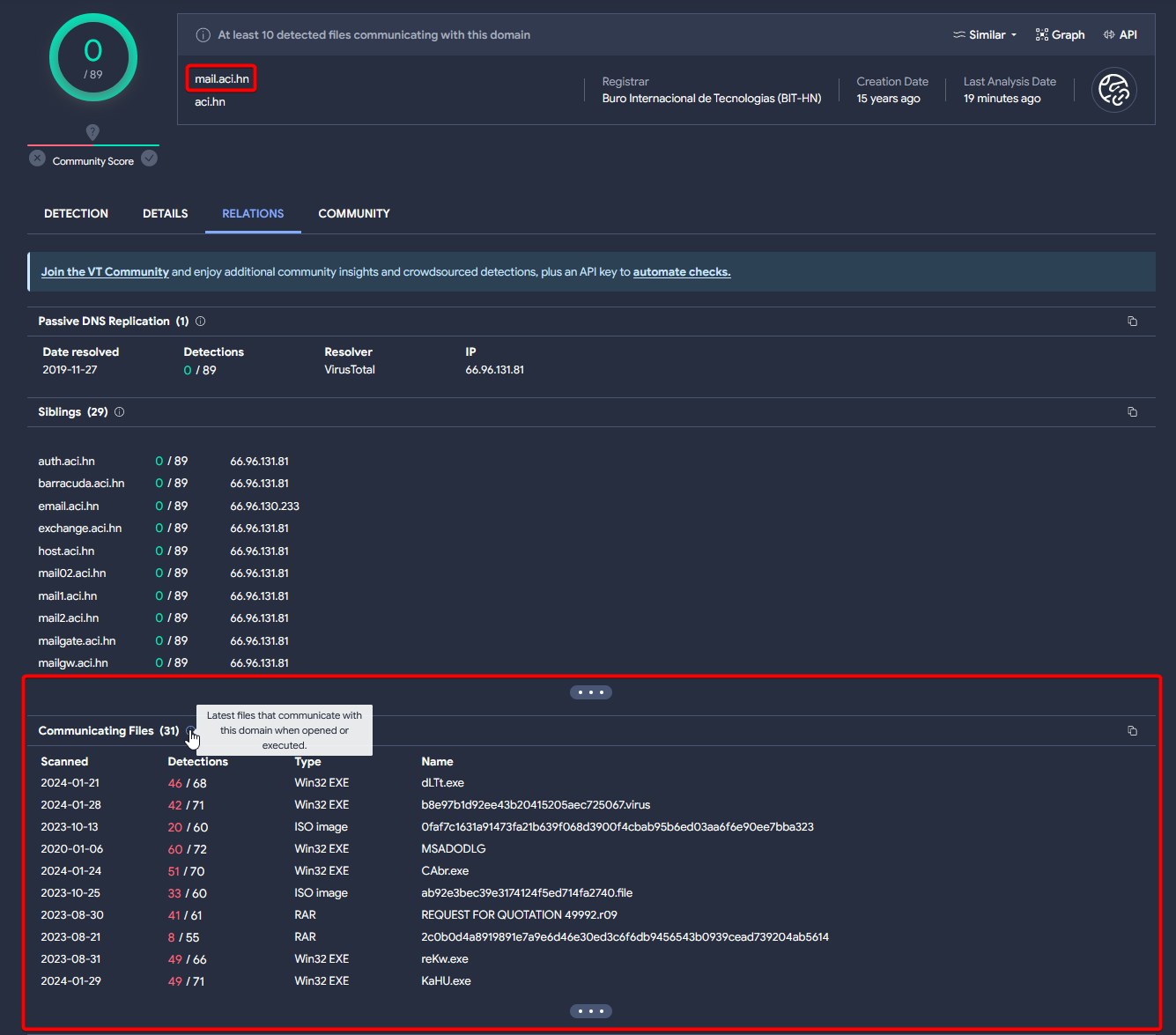
A research at VirusTotal | Source
How to configure the 32Guards sandbox
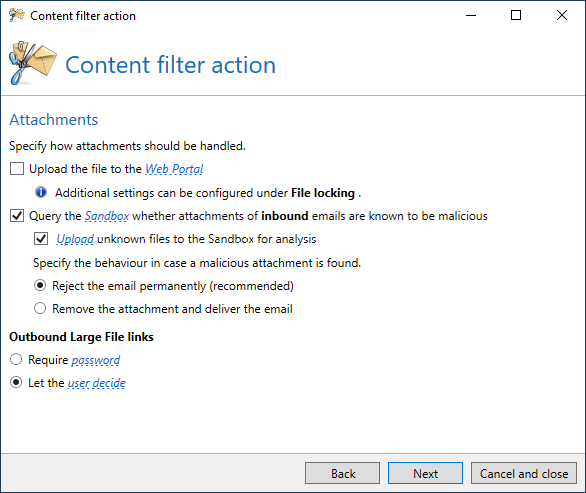
The 32Guards sand box is configured in NoSpamProxy as part of the content filter and can be customised to meet specific requirements.
When a file is uploaded to the sandbox, the email is not accepted in the first step, but temporarily rejected so that the sending email server can deliver it again. Temporary rejection is used here as the analysis takes a certain amount of time, but this should usually be completed after around five minutes when the next delivery attempt is made.
If this delivery delay is undesirable for certain partners, it is possible to configure different actions for “Trusted emails” and “Untrusted emails” in the content filter.
Instead of a sandbox upload, only a sandbox hash query can be performed. In this case, the email is not temporarily rejected, but only the hash value of the attachment is checked against the 32Guards sandbox. If the hash value of the file is unknown, the email is delivered.
Configuring the 32Guards sandbox in the content filter
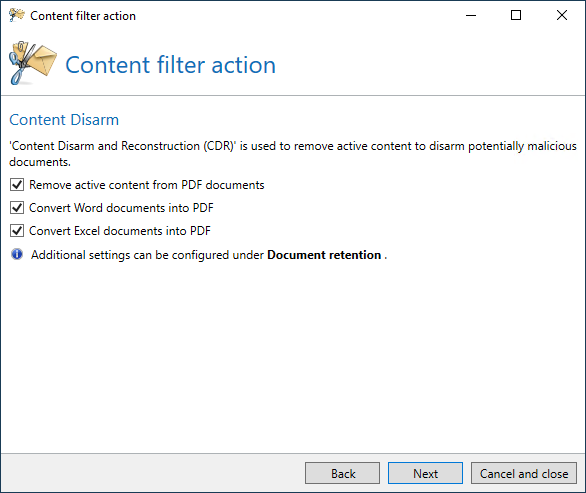
It is therefore necessary to choose between the actions or use other settings in the content filter such as “Content Disarm and Reconstruction” (CDR), which converts Office documents into a secure PDF document.
Configuring options for Content Disarm and Reconstruction
Fewer allowed file types, less of a risk
The file types supported by the 32Guards Sandbox can be found in the documentation. However, it should be noted during configuration that if a file escapes analysis, the email with this attachment will be delivered at the end, provided the other filters and actions in the NoSpamProxy do not take effect.
The question therefore arises as to whether you want to allow potentially dangerous file types for your own company at all, just because they are supported by the 32Guards sandbox, such as the “Executable file for Windows”. In such cases, it often makes more sense to reject such file types in general and thus avoid uploading them to the 32Guards Sandbox.
Documentation
The email firewall remains the best protection
Since the end of 2018, we have been propagating the so-called “email firewall” and recommend prohibiting all file types for the time being and only selectively allowing individual required formats, as with a firewall. So if you have introduced 7-ZIP or WinRAR company-wide for secure ZIP encryption, you should address the potential threats posed by the new but old archive formats supported in Windows – and do so promptly. The data in 32Guards clearly shows that although RAR archives occur less frequently than ZIP archives as attachments in emails, they have a very high probability of containing malware. A strict email policy for the company would therefore only allow ZIP archives and reject the rest.
Not yet using 32Guards Sandbox?
With NoSpamProxy and the 32Guards Sandbox, you can reliably protect your company against cyber attacks. Request your free trial version now!
Note: The 32Guards Sandbox Reports, as shown in this blog article, will be available to NoSpamProxy Cloud and NoSpamProxy Server customers at a later date.