32Guards Reports: Short URLs in a Haystack
Short URL services such as bit.ly are consistently used by criminals to get phishing links past email security solutions and onto their victims’ computers. In this article, we show you how short URLs are used as part of spam campaigns and why 32Guards and its dedicated web crawler offer ideal protection against attacks.
As described in previous articles, phishing attacks using bit.ly links are a popular attack vector. In general, any kind of short URLs should be treated with a certain basic scepticism. 32Guards offers effective protection against dangerous short URLs – but does this also apply to short URL services that are appearing more and more quickly? Let’s take a look at the current situation.
Getting a handle on the data with 32Guards
Running a short URL service is not particularly difficult from a technical point of view. In addition to well-known services such as “bit.ly” or “t.co”, new websites are emerging that offer the creation of short URLs. Phishing attackers are often among the early adopters of these new services.
In order to provide optimal protection, new short URL services should therefore be quickly recognised as such, because only then can the generated URLs be treated with the appropriate caution. The meta data collected by 32Guards, together with the web crawler used, make it possible to look behind the scenes of the short URL services and gather valuable information.
32Guards identifies 60 million URLs per week. Over 1.5 million of these URLs belong to new domains, i.e. domains that have not been sighted before. Filtering out the short URL services from this huge amount is like the proverbial search for a needle in a haystack. It is therefore necessary to first narrow down the large data set.
How to filter out short URLs
Two simple characteristics serve as an indication of a typical short URL:
What is a query string?
A query string is the part of a URL that is introduced by a question mark (?) and ends with a hash (#) or the end of the URL. Such a string often consists of one or more parameters, which in many cases are separated by an ampersand (&).
An example that fits this pattern is the service “flip.it”. The associated URLs follow a simple pattern:
Hxxp://www.flip.it/SAYDaj
Hxxp://www.flip.it/bnwaNO
Hxxp://www.flip.it/dCnGP5
Where do the short URLs lead to?
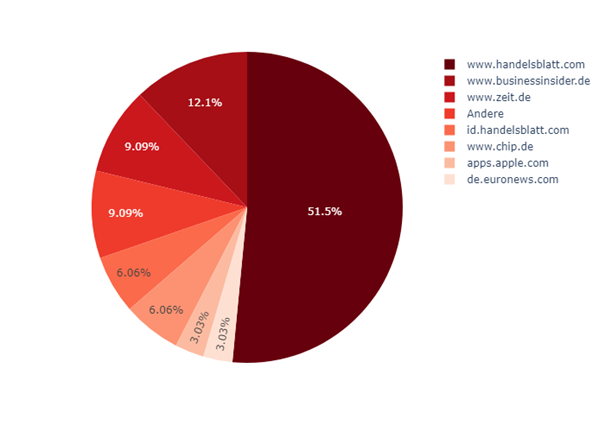
More precise information is provided here by the crawler data. The following graphic shows where the URLs generated by “flip.it” resolve to:
The results make it clear that the service redirects to legitimate (and known) domains. The crawler data allow a safe evaluation.
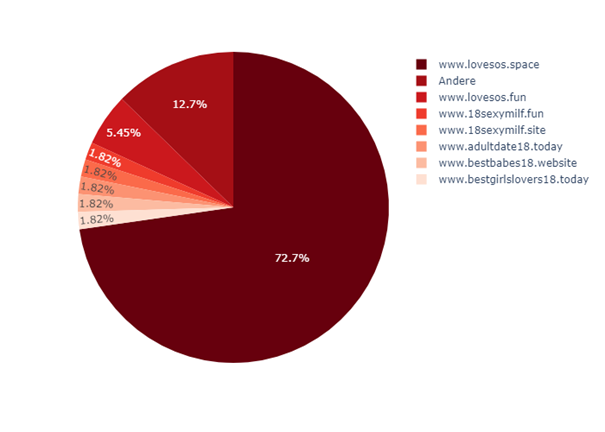
A different picture presents itself when analysing the service “1i.fi”. Here, too, we have a short domain that always occurs in combination with short paths. A look at the destinations of the redirects leaves hardly any questions unanswered:
32Guards can therefore also react quickly here and evaluate the URL shortener domain accordingly.
New services are particularly popular with criminals
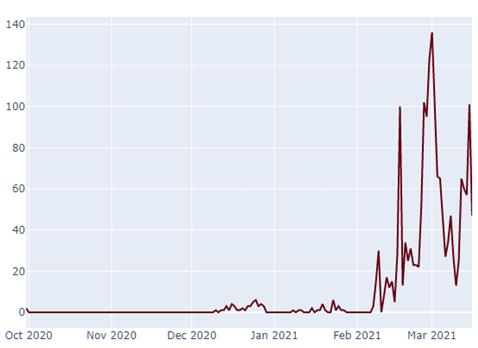
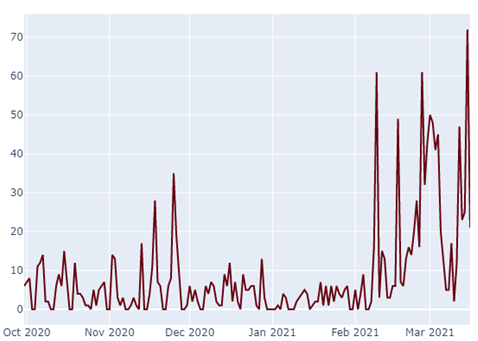
The temporal course of the “1i.fi” sightings also allows for interesting insights:
It becomes apparent that “1i.fi” has only really been in active use for a short time, another indication that it is being used by criminals. 32Guards clearly detects the sudden, increased use of one here at an early stage and can then keep an even closer eye on the corresponding service.
With the two examples shown so far, it was easy to make an assessment, because the targets of the short URLs were easy to recognise as dubious. The situation is different with services like “bit.ly”, which are used for spam attacks as well as for legitimate communication.
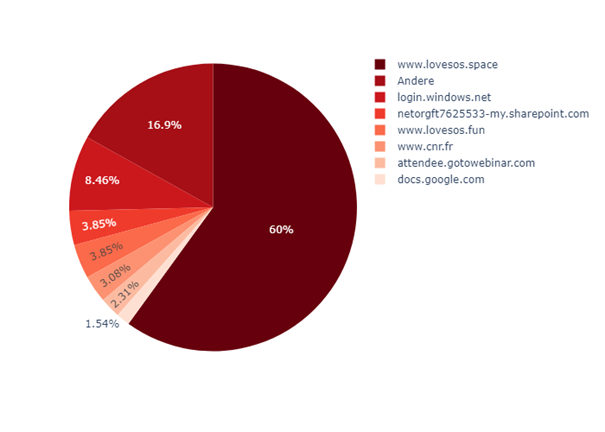
The service „urlz.fr“ is another example:
This service has also been used recently to distribute links to “lovesos.space”. However, there are definitely services among the other links that at least suggest a legitimate use of “urlz.fr”.
A look at the distribution over time is helpful:
Here, too, there has been a sharp increase in the number of hits. It can be strongly assumed that this spam campaign is related to the campaign shown above at “1i.fi” – with the difference that URLs from “urlz.fr” were spotted even earlier.
URL chaining aims to make detection more difficult
In addition to the traditional use of short URL services, chaining is a popular means of making the evaluation of malicious short URLs more difficult. Here, the URLs refer to another service, in some cases even to several in a row. Only then is the actual, malicious target pointed to.
Here is an example of such a chain:
0i.is/153CAIXA –> rb.gy/l4012t –> 0i.is/103CAIXA –> rb.gy/qwkxdj –> 0i.is/cef0 –> gg.gg/ncii6 –>www.atendimentosaconline.com/
First, the short URL services “0i.is” and “rb.gy” are switched back and forth. Before the end of the chain, the service “gg.gg” is added.
Chains like this are the exception rather than the rule, but it still shows the effort that is made in some cases to distribute malware. 32Guards also reliably detects such chains and thus offers secure protection against malicious code that is intended to be distributed via short URLs.
Conclusion
The article has shown how 32Guards recognises new short URL services on the basis of the collected meta data and how an accurate evaluation is possible with the help of web crawling. In this way, 32Guards can quickly identify new developments and adapt its set of rules accordingly: Short URL services classified as suspicious can be analysed more intensively by 32Guards and, if the data is clear, proactively and completely blocked.
Use 32Guards now
The 32Guards action in NoSpamProxy ensures that metadata on emails and attachments are collected and analysed. The goal is to build an even more powerful anti-malware intelligence that can detect and fend off attacks by spam and malware even faster and more accurately. If you are interested in using the beta version of Project 32Guards, send an email with the subject “32Guards activation” to NoSpamProxy Support and attach a screenshot of your licence details.