Microsoft announced as early as February 2022 that it would prevent the execution of macro functionality in Office documents if these documents originate from the Internet. At the beginning of July, Microsoft temporarily stopped the announced rollout and then reversed it to finally continue with said rollout on July 20. In the meantime, the malware authors have been looking for new social engineering mechanisms away from Office documents and are already planning for the time without the tried and tested vehicle of macro functionality.
Digital Matryoshka foisted in large HTML attachment
In July, QakBot started using HTML attachments with names like “FXS_3733007.html”, “TXRTN_2143642.html” or “Report Jul 14 39523.html” as well as a rather appealing “Adobe Template”. The attachments, which were quite large for spam at over 1 MB, were conspicuous. As a rule, spammers want to reach as many recipients as possible in a short time before the attachment is recognised by anti-malware products. So there must be more behind such a large HTML attachment than is apparent at first glance.
The HTML attachments in question were used in the context of so-called “email reply chain attacks“, i.e. fictitious replies to authentic email communication that had previously been diverted. In this way, the attackers make sure that the potential victim thinks he is safe, since he really sent the original email. However, the reply with the HTML attachment then comes from the attacker.
Double-clicked and smuggled into the downloads folder
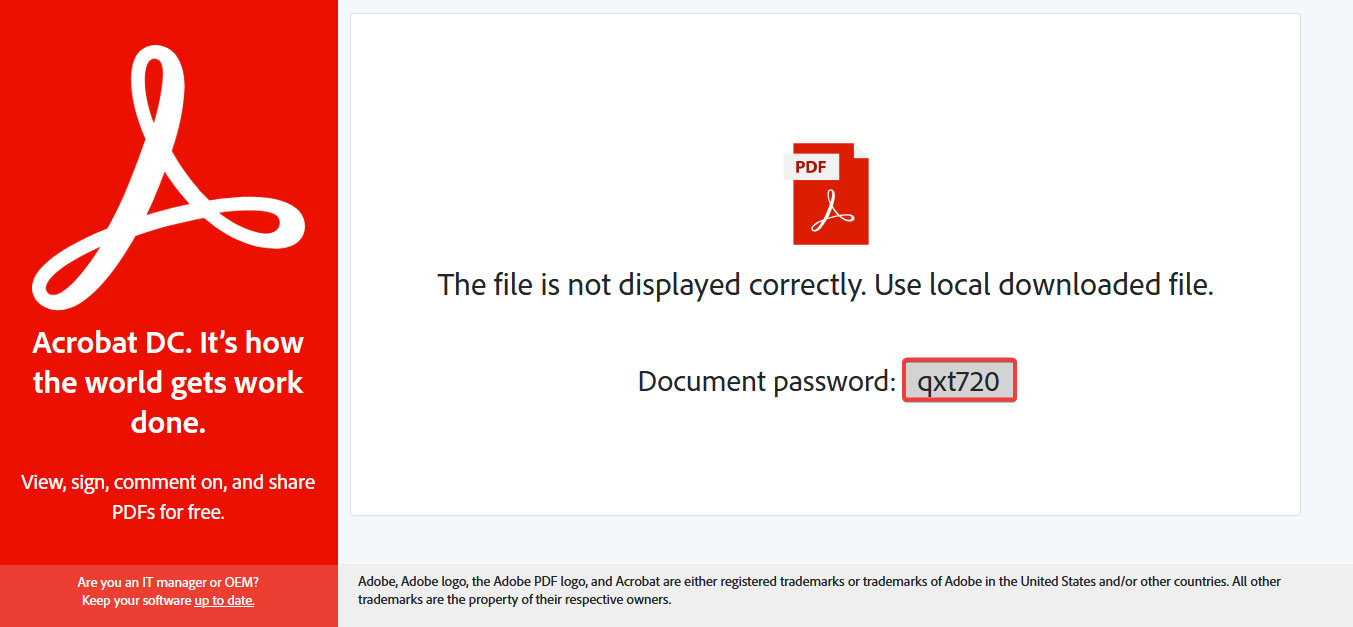
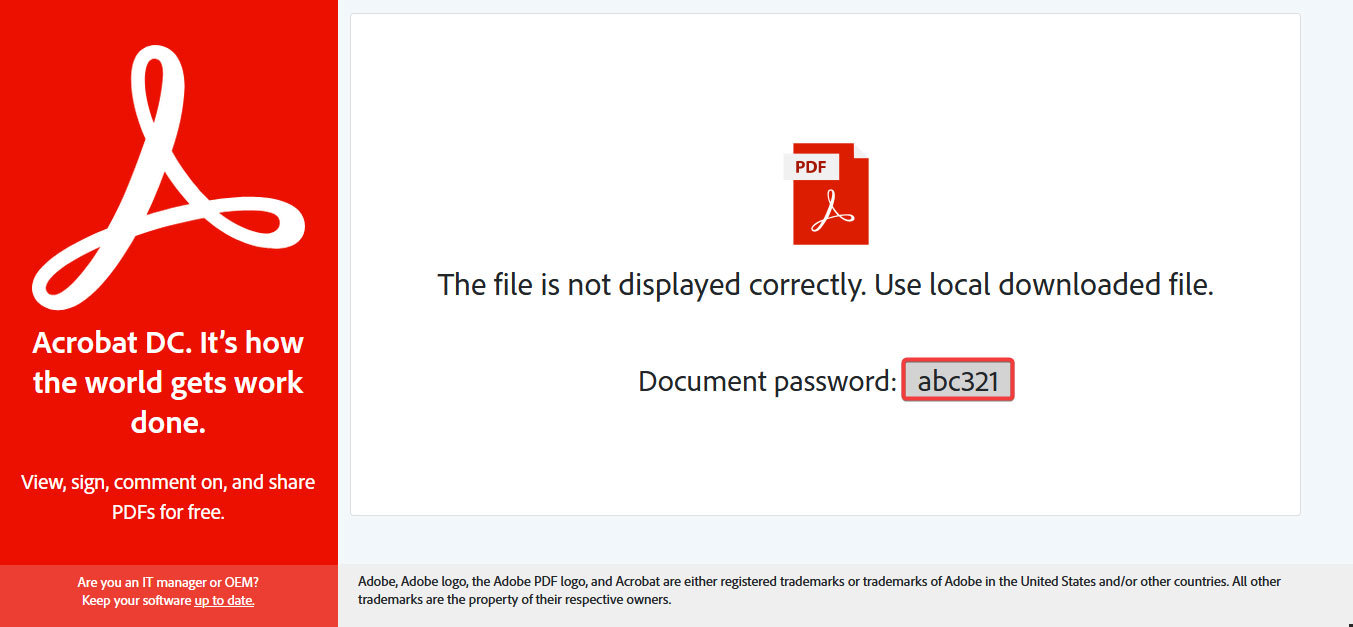
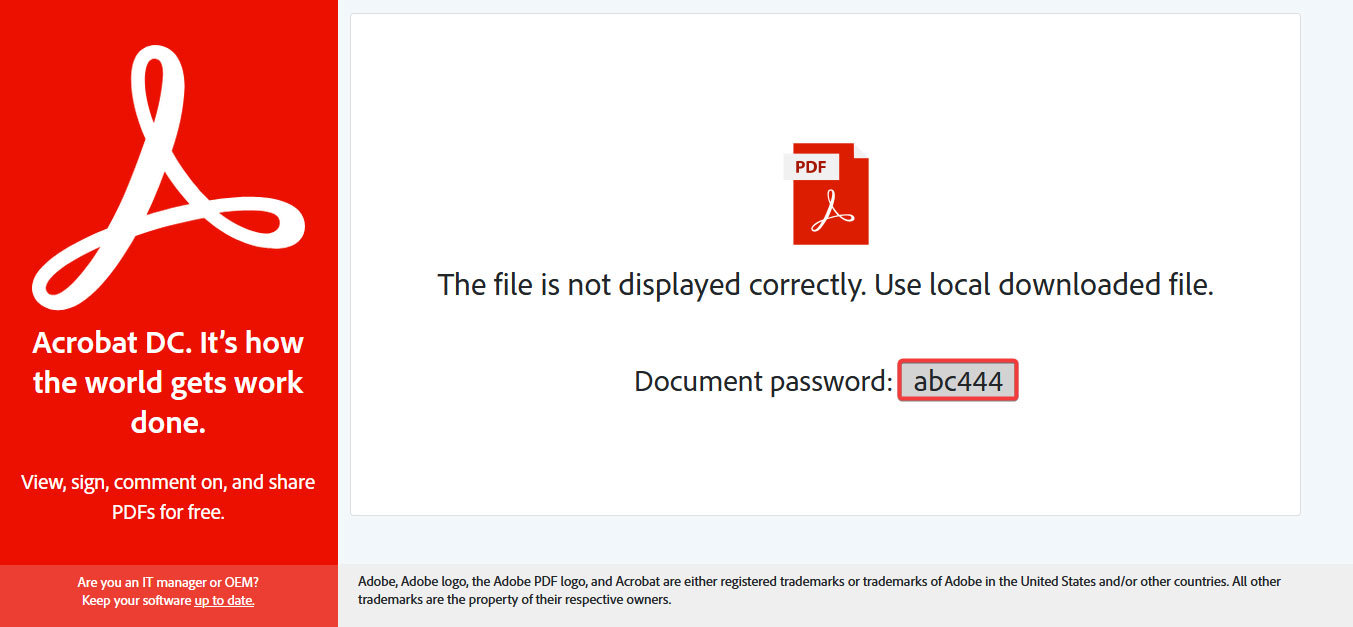
After double-clicking, the HTML attachments open in the browser and the download conveniently begins automatically, and without any further interaction, the “smuggled file” in the HTML document is loaded from it into the “Downloads folder”. Since the alleged PDF document cannot be displayed, reference is made to this download.
Many malware scanners are useless with archives.
The download is a password-protected ZIP archive that is located in the HTML file. Conveniently, the password is then also presented in the browser. Due to the password protection, the archive cannot be identified as malicious by malware scanners without an on-access component, as they cannot scan the inside of the archive without the password.
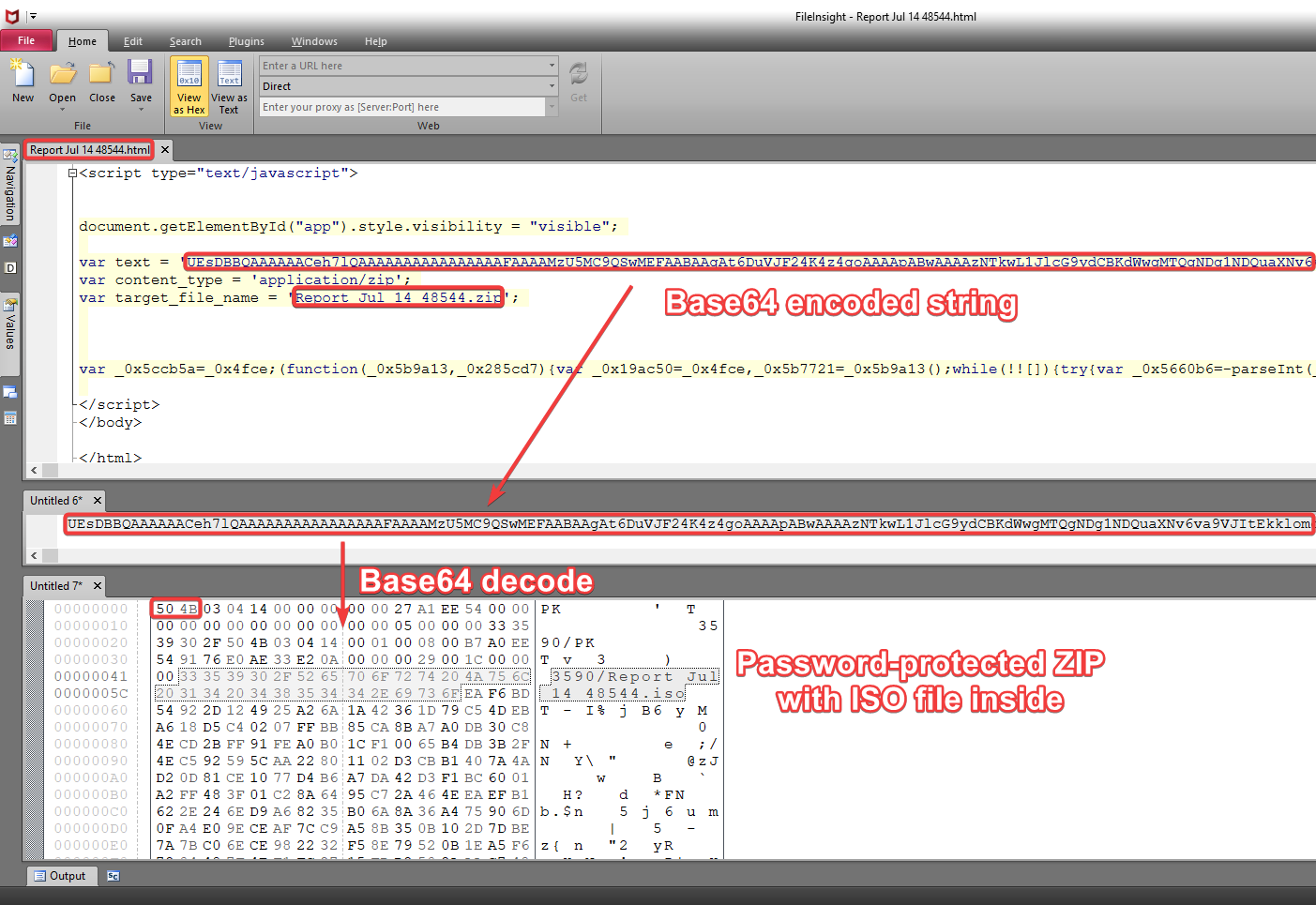
HTML attachment analysed in the editor. The variable “text” contains a Base64-encoded string that contains the password-protected ZIP archive, which in turn contains an ISO image.
In the archive itself, there is an ISO image in a subfolder. Just like a matryoshka, the deeper you dig with the digital counterpart, the more surprises you will find.
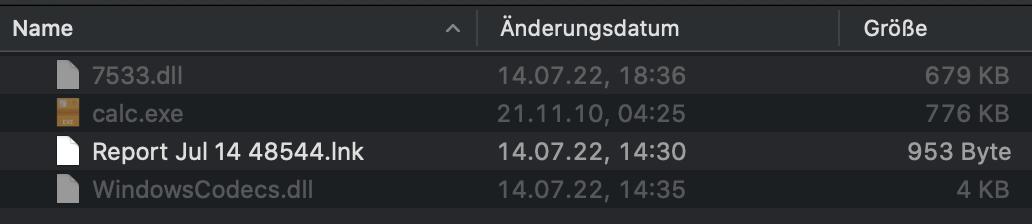
The “hidden” content in the ISO image with all file extensions.
If you open the ISO image from our example with a double click in Windows, you will initially only see a file with the name “Report Jul 14 48544”. Only when the “hidden” files and the known file extensions are also displayed, does one realise that the file is a malicious LNK file. However, this only launches a “calc.exe”.
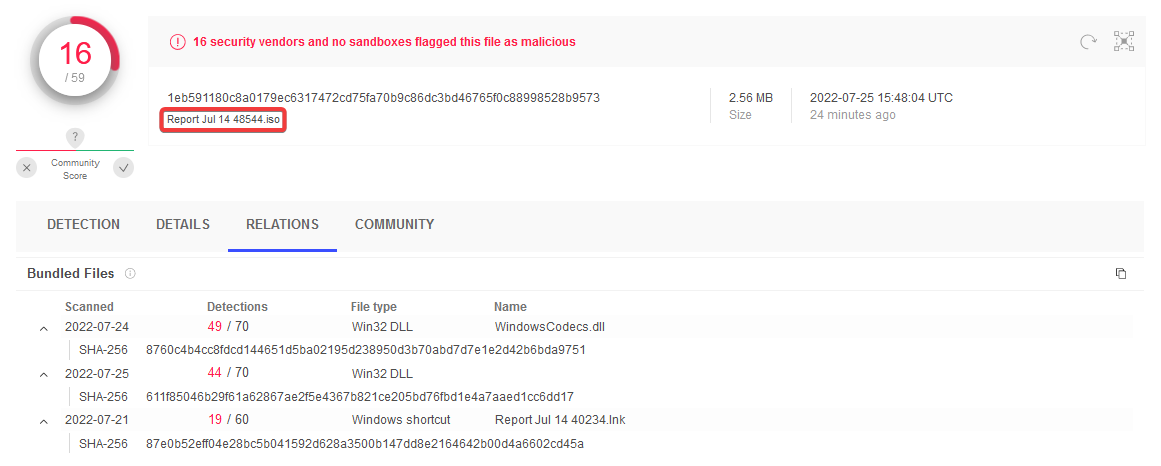
VirusTotal overview of the files in the ISO image
Source: VirusTotal
The “calc.exe” is an older but legitimate Windows program and originates from Windows 7, but the “WindowsCodecs.dll” is malicious. The trick used here is known as “DLL Search Order Hijacking” and leads to Windows not loading and executing Windows’ own “WindowsCodecs.dll” when “calc.exe” is started, but the DLL with the same name deposited by the QakBot authors in the same path. An analysis can also be found here.
Non-breaking news: email firewalls are a must
We have been propagating the so-called “email firewall” since the end of 2018 and recommend banning all files by default and only selectively allowing individual required formats – as with a firewall. Now that QakBot has discovered “HTML smuggling” as a vehicle, the topic should definitely be pushed to the top of the priority list and at least the handling of HTML attachments from partners without a level of trust should be treated much more restrictively (see recommended action here).
You would like to protect yourself from QuakBot and do not yet use NoSpamProxy?
With NoSpamProxy you can reliably protect your company against cyber attacks. Request your free trial version now!