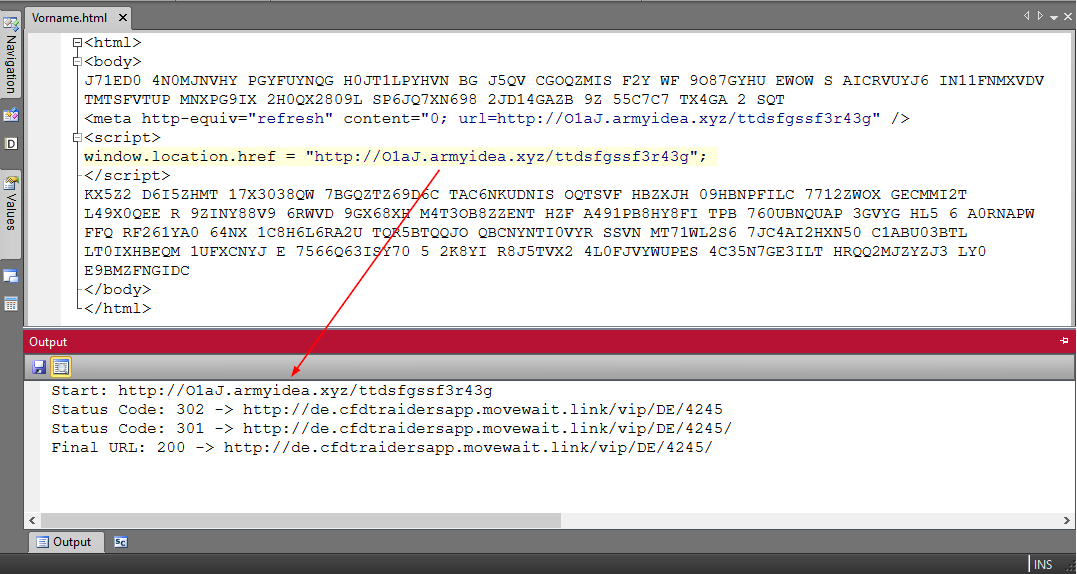
Actual HTML attachment from a spam email, which additionally disguises the actual destination of the URL by HTTP redirects. These HTML attachment spams are usually sent by well-known freemailer services such as Hotmail, GMAIL or Outlook.com.
If you compare such HTML attachments with Office documents with macro functionality, you will notice that Microsoft has built up much stronger protection mechanisms in recent years. Users must first confirm the relevant information before the macro is even executed. Optionally, the execution of macros in the company can be disabled via group policy and exceptions can be defined.
At the beginning of February 2022, Microsoft also announced that it would soon be taking an even stricter approach to such Office documents. In future, the execution of Office documents with macro functionality will be prevented by default and users will no longer be tempted by social engineering tricks to confirm the corresponding dialogs.
For this purpose, Microsoft wants to rely on the NTFS feature “Mark of the Web” (MOTW for short). This feature allows the company to trace which documents originate from the Internet. If the macro is not signed, this is a popular gateway for spammers. There are hardly any comparable protection mechanisms for HTML documents, which are rendered in the browser after a double click.
Content filter for handling direct HTML attachments
With the content filter in NoSpamProxy you can filter HTML attachments according to your own requirements.
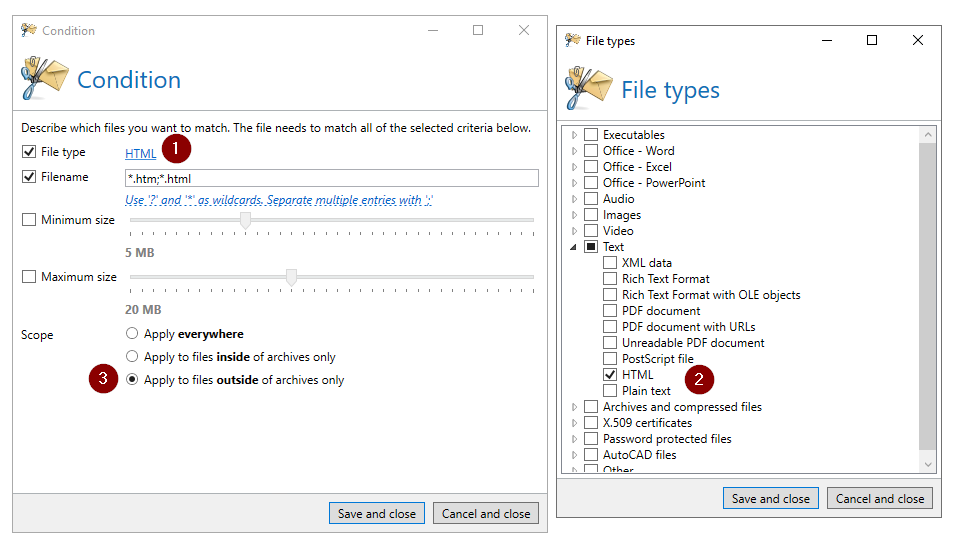
The file type HTML can be found in the Text category. For targeted filtering of direct email attachments, the condition should only be applied outside archives. Additionally, the file name can be restricted to include the pattern “*.htm;*.html”.
Such direct HTML attachments can then be moved to the NoSpamProxy Web Portal or removed from the email. Alternatively, the entire email can be rejected. This is controlled by assigning a corresponding action to the new content filter entry. By applying the Level of Trust system, one can also limit this only to emails from untrusted communication and exclude HTML attachments from partners with a corresponding trust bonus from filtering.
If even more granularity is desired, an entry can also be created under “Partners” for “outlook.com” and other freemailer services, and only these domains can then be assigned the tightened content filter.
Note: If an incoming content filter is also stored on the company user side at the same time, NoSpamProxy always uses the filter with the stricter settings.
HTML attachments are also in use in legitimate contexts, for example at DATEV eG. This happens if no S/MIME certificate is available. In this and comparable cases, one should configure a fixed level-of-trust bonus of 50 points for the partner or define an exception for the file name.
Protect yourself from dangerous HTML attachments with NoSpamProxy 14.0 and Cloud
In NoSpamProxy version 14.0, which is also the backbone of NoSpamProxy Cloud both in the shared stack and in the private stack, customers are already better positioned against this example from the screenshot above. The Spam URI Realtime Blocklist filter in 14.0 also parses URLs from text-based attachments such as HTML or also RTF, XML and others and also matches these with NoSpamProxy Cloud as well as external services.
What is HTML smuggling?
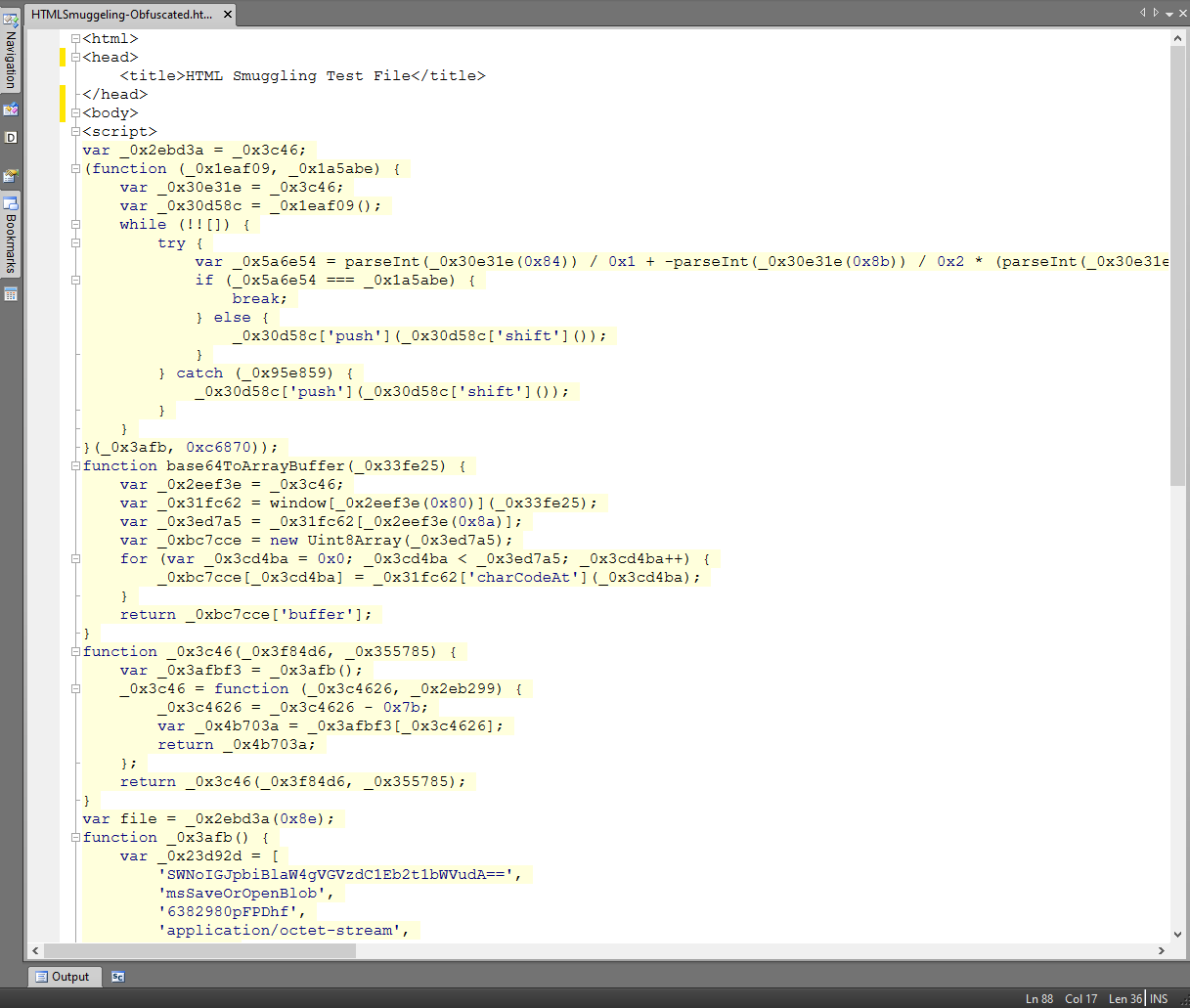
A particular threat arises from so-called HTML smuggling, to name just one other possible attack vector, which could arise in conjunction with HTML attachments. Here, modern functionalities such as JavaScript blobs and/or HTML 5.0 are used to hide entire files in an HTML document.
HTML Smuggling test file with an additional JavaScript obfuscation layer.
Such attack methods have so far been seen more in highly targeted attacks on very exposed targets.
A harmless HTML file, or not?
It is safe to assume that attacks via HTML attachments will become more widespread in the future, as Microsoft is making it increasingly difficult to distribute malware via Office documents with macro functionality.
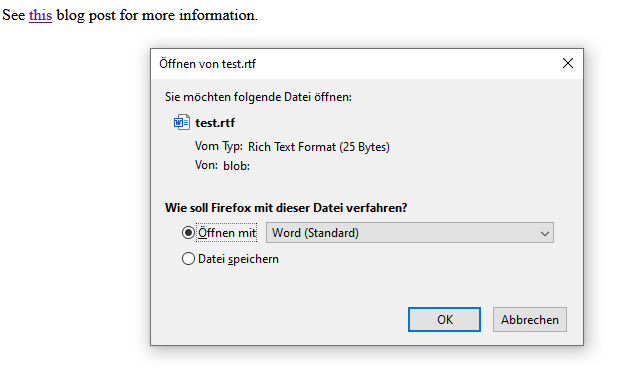
A double-click and the HTML attachment is opened in the browser, the JavaScript code is executed without further prompting and a harmless test file, which was located in the JavaScript code, is loaded. This could also have been a password-protected archive with malware, and the corresponding password for it is located separately in the text of the email.
We have been propagating the so-called email firewall since the end of 2018 and recommend banning all files for the time being and only selectively allowing individual required formats , just ike a firewall. So it’s best to deal with the potential threat of HTML attachments in emails now and not wait any longer.
Not yet using NoSpamProxy?
With NoSpamProxy you can reliably protect your company against cyber attacks. Request your free trial version now!