About mealybugs and ladybugs
The US company Symantec has established the term “Mealybug” for the actors behind the Trojan Emotet, which translated would be the mealy bug. The natural predators of mealybugs include ladybugs, and in Australia a special type of ladybug (Latin: Cryptolaemus montrouzieri) is bred and marketed. Thus, the name of the unofficial “Emotet Working Group” was born out of a worldwide collective of IT security experts* who together fight the emotet botnet and network via Twitter. The collected IoCs (Indicators of Compromise: daily updated indicators for emotet detection) from the Cryptolaemus team are consumed by 32Guards and are available in the 32Guards beta.
Optimise Existing Protection Through Optimal Configuration
All NoSpamProxy customers currently participating in the 32Guards beta are currently protected by 32Guards’ warnings in many cases. Nevertheless, it is highly recommended to configure the system locally in the best possible way to meet the current situation.
Check Password-Protected Files Carefully
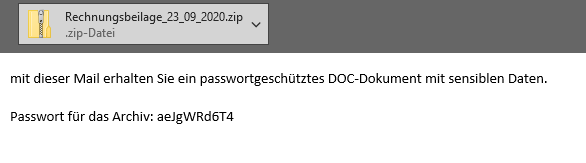
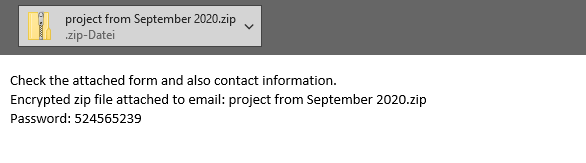
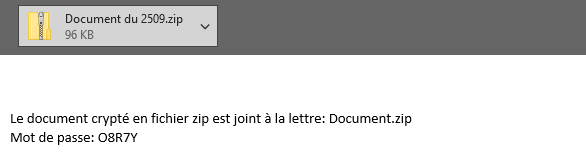
In general, the best practice recommendation for encrypted content is not to deliver it without checking for spam, malware or policy violations. As described above, the danger with encrypted ZIP archives is currently very high due to the Emotet operation “Zip Lock”. Anyone who has not yet thought done so is well advised to define an approach to password-protected files for their company as soon as possible and to implement it accordingly in NoSpamProxy.
Since 2018, we strongly recommend to use a whitelisting approach for content filtering (keyword: Email firewall). Customers who have already implemented this may not need to take any action at all; this was not previously required in the workflow in the respective companies, for example when files were securely shared via the cloud or NoSpamProxy Larges Files.
Configuring content filters correctly
Since NoSpamProxy Version 13.1, the file type “Encrypted ZIP-compressed file” is explicitly available in the content filter. So it is possible to block these files first and upload them to the Web Portal. Only after manual approval by the administrator does the relevant attachment become available to the end user. Of course, it is also possible to create content filter entries that can differentiate between emails without trust (such as the current spam wave) and those from regular communication partners (which have been identified accordingly by Level of Trust).
Use 32Guards Now
The 32Guards action in NoSpamProxy collects and analyses metadata about emails and attachments. The goal: to build an even more powerful anti-malware intelligence that can detect and fend off attacks by spam and malware even faster and more purposefully. If you are interested in using the beta version of 32Guards, send an email with the subject “32Guards activation” to NoSpamProxy support and attach a screenshot of your license details.