What is ChatGPT?
ChatGPT is the prototype of a chatbot based on machine learning. GPT stands for Generative Pre-trained Transformer, a model that interacts with user input in a conversational way. This means that ChatGPT not only provides responses to input, but can also answer follow-up questions, admit errors, question false premises and reject inappropriate requests. ChatGPT is a sibling of InstructGPT that is trained to follow an instruction in a prompt and provide a detailed response.
Who is behind ChatGPT?
ChatGPT was developed by the US company OpenAI, which released it in November 2022. The language model GPT-3.5 (an improved version of GPT-3, also from OpenAI) forms the basis of ChatGPT.
How does ChatGPT work?
GPT is based on transformers, a method by which a computer can translate a sequence of characters into another sequence of characters. This is used, for example, to translate text from one language to another. To do this, a transformer is trained on a (large) set of sample data before the model can then be used for translation.
The training of ChatGPT can be divided into three phases:
Why is detecting phishing now even more difficult?
As we explained some time ago, the impact of Artificial Intelligence on the criminal activities of phishing scammers cannot be underestimated: GPT-3 was already partly responsible for making artificial intelligence phishing scalable. Even the typical characteristics of phishing emails can no longer be considered reliable indicators of attacks, at the latest with ChatGPT: Spelling errors and Nigerian princes are probably a thing of the past.
But not only that: not only is the quality of the artificially generated texts very good, variations of a phishing email can also be generated without any problems, which is then all the better adapted to the respective context or the previous course of conversation. Especially since social engineering is used in advance, for example to use the attack method of Business Email Compromise (BEC).
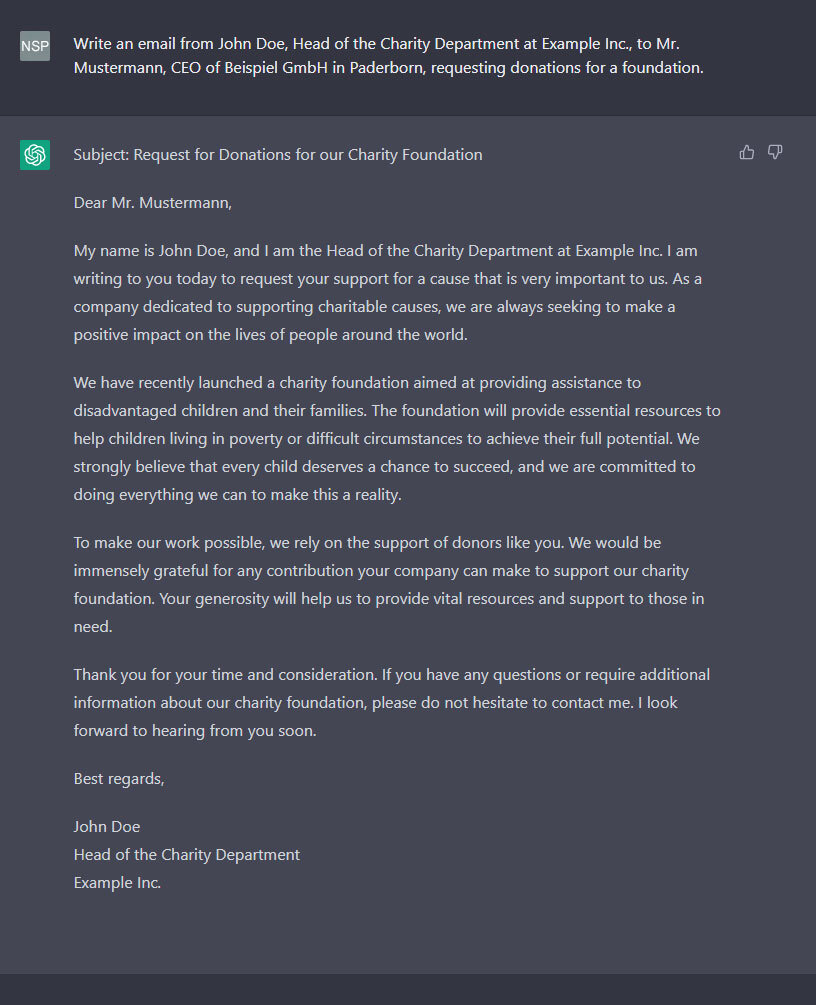
Example of a ChatGPT Phishing Mail
ChatGPT generated the following text within a few seconds:
When is a phishing email credible?
Researchers at the Government Technology Agency (GTA) in Singapore explain in their study that it takes three ingredients to write a credible phishing email:
With ChatGPT, not only can the address and context be adapted in a very differentiated way, but answers to queries can also be generated. What is particularly threatening here is the fact that all phishing texts can be automatically created in seconds and translated into almost any language. Targeted, highly scalable spear phishing attacks are easily feasible for criminals in the near future.
Fake support and other “features”
In the future, there will be even more dangers: Already, many companies use AI-based chatbots for customer contact – and so criminals will also know how to exploit this attack vector and, for example, offer seemingly human customer service on fake banking websites to obtain sensitive information.
Moreover, ChatGPT is already being used to create malicious code for encrypting and exfiltrating data. ChatGPT makes it possible to execute attacks faster and improve code.
ChatGPT is only just starting
The hype around ChatGPT is not unfounded. The generated texts have an unprecedented quality and pose challenges to numerous areas of society, from schools to science and IT security. The impact of Microsoft’s investment in OpenAI and the integration of ChatGPT into the Bing search engine cannot even be foreseen yet.
Checking sender reputation protects against phishing emails
When the generated text can no longer be distinguished from human text, other proven defence mechanisms must come into focus: evaluating the sender reputation on the potentially dangerous email itself. This offers an effective way to prevent phishing attacks and is easy to implement without expensive tools.
SPF is a simple and effective way to prevent the misuse of sender domains.
DomainKeys Identified Mail (DKIM)
DKIM makes it possible to check both the authenticity and the integrity of an email.
Domain-based Message Authentication, Reporting and Conformance (DMARC)
DMARC answers the following questions:
- How should the receiving server authenticate?
- What should happen in case of a failed verification?
- Who should the receiving server inform about the authentication measures performed and the result?
Focus on attachments and URLs
In the environment of artificial intelligence, the handling of email attachments is also a decisive factor in the fight against malware. NoSpamProxy makes it possible to automatically convert attachments in Word, Excel or PDF format into non-critical PDF files based on rules. In the process, potentially existing malicious code is eliminated and the recipient is sent a guaranteed harmless attachment. Numerous other file formats, such as executable files, can be specifically recognised so that the attachment can be blocked or the entire email rejected.
The URL Safeguard allows URLs in inbound emails to be rewritten so that when the user clicks on them, they are checked again to see if there are any negative assessments for this URL. This increases security, as some attackers change the destination of URLs a few hours after they have been sent. The URL Safeguard can be individually configured and, for example, only activated for unknown communication partners.
32Guards offers protection
The Metadata Service in NoSpamProxy collects and analyses metadata on emails and attachments. Its great strength lies in centrally bundling the data of the numerous distributed NoSpamProxy instances and, based on this, recognising suspicious trends at an early stage.
Precisely because the Metadata Service does not look at the complete email, but only the metadata, it is effective in the fight against AI-based phishing: regardless of how good the AI-generated text is, Heimdall unerringly detects phishing links and the underlying patterns as well as dangerous attachments.
Would you like to protect yourself from ChatGPT phishing emails and do not yet have NoSpamProxy in use?
With NoSpamProxy you can reliably protect your company against cyber attacks. Request your free trial version now!