What is DomainKeys Identified Mail (DKIM)?
Just like SPF, DMARC and ARC, DKIM is an essential technology for the detection of forged sender domains and for the defence against phishing attacks. SPF and DKIM have the greatest similarity here: while SPF can be used to ensure whether a server is authorised to send emails, DKIM can be used to check whether an email was actually sent by the owner of the specified domain and whether the email was modified during transport.
DKIM thus makes it possible to check both the authenticity and the integrity of an email. The procedure was originally developed by Yahoo and Cisco, but was supported by an increasing number of companies and finally submitted for standardisation.
How does DKIM work?
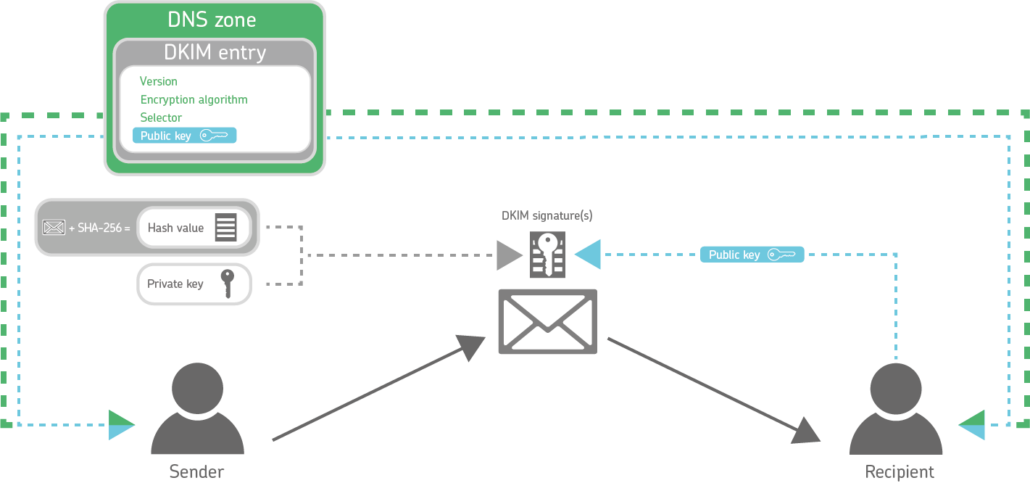
The basis of DKIM is the use of a key pair consisting of a private and a public key, similar to asymmetric encryption.
How to send DKIM-protected emails
First, a hash value is calculated for each outgoing email from the content of the email and parts of the header based on the SHA-256 algorithm. SHA1 has become obsolete as an encryption algorithm and may no longer be used according to RFC 8301. The header fields used to calculate the hash must be specified in the DKIM signature. A hash value is nothing more than a long string of characters.
Using the private key, the sending server now signs the calculated hash value using the RSA procedure or the Ed25519 procedure and adds this signed hash value to the header of the email as a signature.
How to receive DKIM-protected emails
Before this, the sender has stored his public key together with further information as a DKIM entry in the Domain Name System (DNS) of his domain. This enables the recipient of the respective email to check the signature and the hash value.
To be more precise, the receiving server of a DKIM-protected email first determines the sender domain of the email by reading its ‘Header From’ field. There it also finds the so-called selector. The selector indicates under which name the matching public key can be found in the DNS zone of the sender domain.
If the check of the hash value fails, there is either a wrong public key or the email was changed on the way.
The DKIM signature thus ensures two things:
- The receiving server knows that the email and its contents have not been modified in transit.
- The receiving server knows that the owner of the sender domain specified in the header is really the sender.
What does a DKIM record look like?
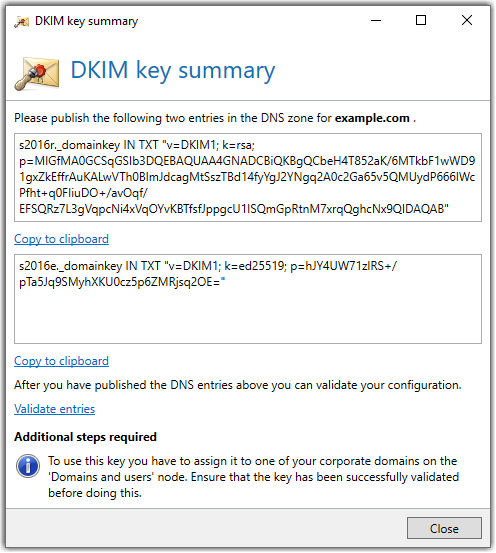
As with SPF, with DKIM the sender creates a TXT record in the DNS zone of the domain to be protected on the basis of an RFC-standardised syntax. The DKIM record consists of the following elements:
Example of a DKIM entry
How to check your DKIM record
With the help of tools such as mxtoolbox, you can quickly and easily check whether there is an DKIM record for your domain.
Notes on the use of DKIM in your company
The use of DKIM is low-risk. When creating the DKIM signature, the sender only has to make sure that the email is not changed afterwards. He must attach any disclaimers or simple signatures to the email in advance. Otherwise, the signature would break because the hash value calculated when sending the email would change. Ideally, the DKIM signature is applied by the last Mail Transfer Agent (MTA) in the sender’s own email chain.
If DKIM signatures are to be checked when receiving emails, this should be done as early as possible – ideally on the first Mail Transfer Agent (MTA) in the email chain. After the check, many systems leave the signature in the header of the email so that it can be checked again later if necessary. This procedure is also recommended.
A special feature of DKIM is the fact that an email can also contain several DKIM signatures. This is possible, for example, if each server in the email chain applies a signature. Within the scope of the DKIM check, all existing signatures must be checked. As soon as the result of a signature is positive, the check is considered to have been successfully passed.
The difference between DKIM and S/MIME
Unlike the cryptographic signatures created using S/MIME, the recipient of an email does not see the DKIM signature. It is a purely server-based procedure. Only when the header of an email is displayed does the DKIM signature become visible.
DKIM and DMARC
As with the use of SPF, the results of the DKIM check leave open the question of the sender’s intent. This information gap is closed with a DMARC policy. In this policy, the sender declares unequivocally how his outbound emails must be protected with which technologies and how the emails are to be handled in the event of an error. Furthermore, the domain holder can be informed about the results of the check.
How to create a DKIM entry
Set up DKIM and improve email security
With DKIM, you can check the authenticity and integrity of emails and thus protect yourself and your company against phishing and spam. DKIM is an important building block for improving email hygiene, but should always be accompanied by SPF, DMARC and ARC. NoSpamProxy is the easiest way to generate and verify DKIM keys.