Inside Emotet: 3 current examples and how Project 32Guards can protect you
Much has been written lately about Emotet and the consequences that an infestation with this banking Trojan can have. Among other things, public institutions have had and are struggling with the consequences of successful cyberattacks that have polluted and crippled their respective IT infrastructures, with sometimes catastrophic consequences. The Berlin Chamber Court is perhaps the best-known example, as large amounts of data could probably be stolen over several days. A real IT total damage. We have already explained how you and your company can protect yourself from emotet elsewhere.
But what does an emotet email actually look like? Three concrete examples show how authentic emotet emails now look. All three examples have been reported to us and have only been anonymized by us to the extent necessary for data protection reasons.
What is the 32Guards project?
32Guards is a project of the NoSpamProxy team to detect attacks on corporate and government networks. 32Guards makes use of the data exchange between different instances of the spam filter NoSpamProxy Protection. Collects information about detected threats and anomalies, significantly increasing the level of protection of all participating NoSpamProxy customers.
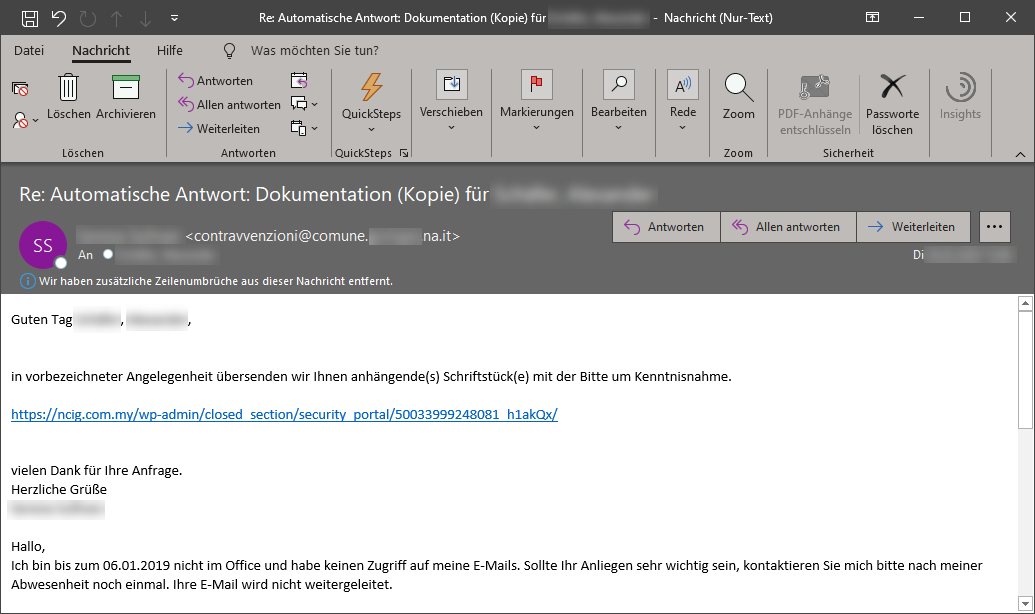
Example 1 – Reply mail with link to malicious code
This email is a good example of how emotet emails creep into existing communication histories. In this case,the subject contains a reference to previous emails , but not only that: The original absence note of the recipient is also part of the e-mail, which further lowers the inhibition threshold for clicking. The e-mail address displayed in the header of the e-mail indicates a municipality in Italy as the sending domain and a sending namethat does not appear in the e-mail address. Very suspicious. Searches revealed that it was actually sent from that domain and that the affected municipality had apparently previously been the victim of a hacking attack. However, one should be sceptical at the latest with the attached link: The domain ending my for Malaysia in connection with a reference to a WordPress installation (wp-admin) is a strong indicator that there is no document but malicious code stored there.
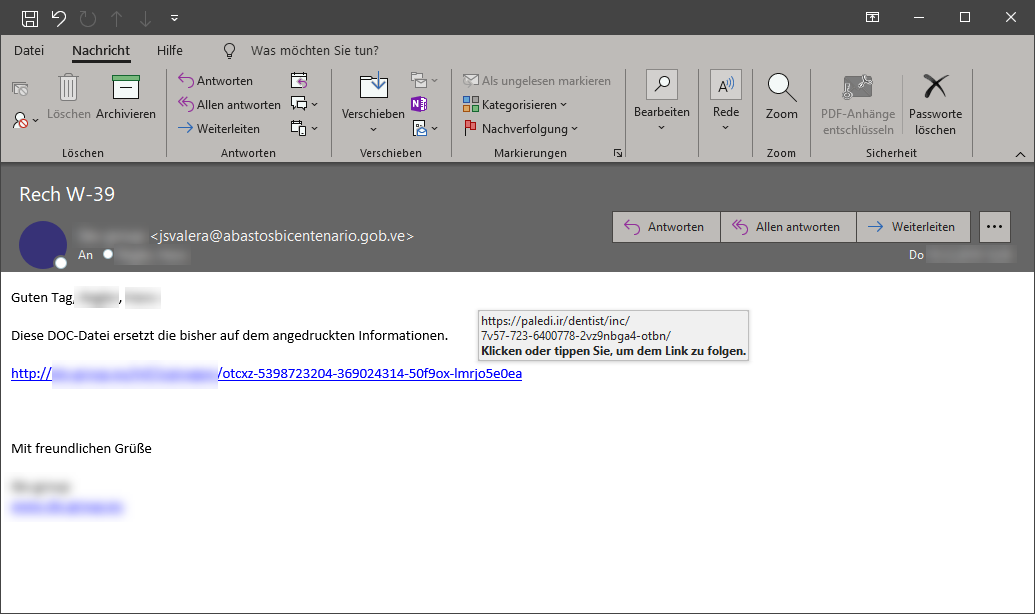
Example 2 – Link with different destination
The domain ending ve for Venezuelais striking here. What is not recognizable due to the anonymization: Also the specified sender name shows no connection to the sender address.
If we ignore the erroneous grammar within the e-mail, all the alarm bells should ring in the inserted link: the displayed link address is a completely different from the actual link address (which becomes visible when the mouse pointer is moved above the displayed link).
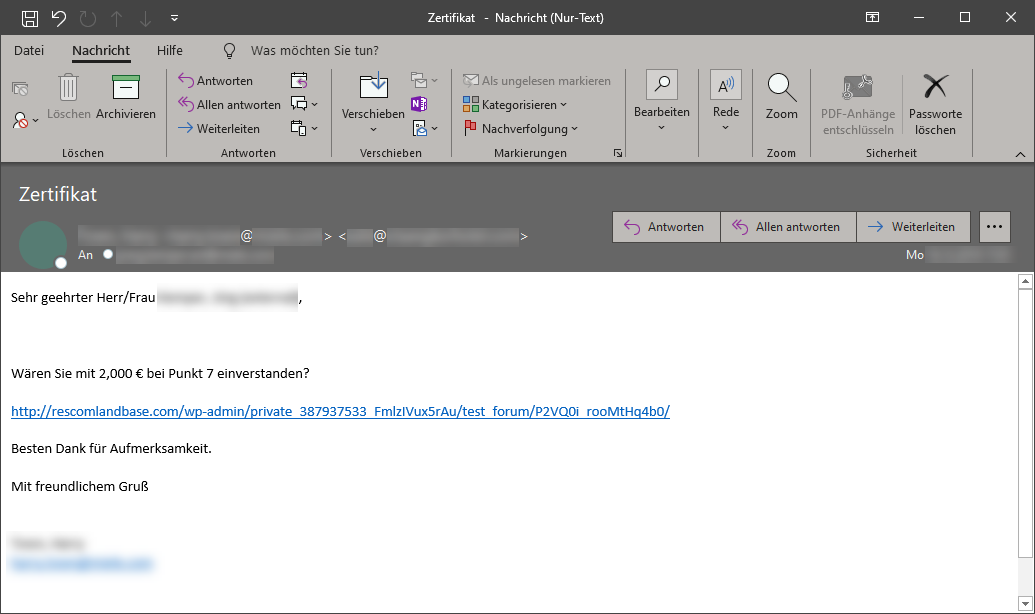
Example 3 – Two sender addresses in the header
The unique indicator that something is lazy with this e-mail is the two sender addresses in the header. The attackers speculate here either that when viewing on a desktop PC or laptop only the first address is observed or that this e-mail will be opened on a mobile device — in the latter case, only the first address is usually displayed. Not recognizable due to anonymization: The company name appears in the first address, but the wrong domain ending is used. Again, the attached link contains the reference to a WordPress installation,which is supposed to spread malicious code with a probability bordering on security.
Project 32Guards would have ensured protection
The 32Guards action in NoSpamProxy collects and analyzes metadata about emails and attachments. The goal: to build an even more powerful anti-malware intelligence that can detect and fend off attacks by spam and malware even faster and more purposefully.
For this purpose, suspicious links are collected and compared with database entries of known, evil links. If a link is found to be defective, it is immediately blocked or the e-mail is rejected. In addition, the 32Guards project monitors the e-mail traffic of all connected NoSpamProxy instances in real time —for example, whether certain links are distributed multiple times in a short period of time, whether existing virus scanners have already detected links as malicious, or whether new domain extensions are used unusually often. In all the cases shown, the links contained would have been blocked or the e-mail rejected. The companies concerned would have been protected from Emotet.
What about attachments?
Contaminated email attachments are also used to spread emotet and other malware. Here, the 32Guards project provides protection against archives with outdated endingsthat can still be processed by many archive programs, but often slip through spam filters. These archives can hide a variety of types of malicious code. The 32Guards project is able to detect and block them.
Often the criminals also try to smuggle files through as PDFs,even though they are executable files (.exe) for example. The attackers achieve this by using endings such as pdf.exe or pdf.iso. The 32Guards project detects this and blocks the file or adjusts the spam confidence level accordingly. Not only that: The 32Guards project also learns the patterns behind such attacks and can react to them faster and more precisely over time and with an increasing number of 32Guards users.
Another important application scenario is the evaluation of file hashes. If the same and previously unknown hashes suddenly appear under many different file names, this is a clear indicator that they could be contaminated files.
View
The basis of Project 32Guards’ approach is the establishment of a chain of circumstantial evidence,which enables evaluation in the first step and the processing of an e-mail in the second step. As described above, this chain of circumstantial evidence already exists and provides impressive results. The development of Projekt 32Guards will of course continue and will also expand the real-time protection area. This allows new malware trends, novel spam attacks and emerging threats of all kinds to be detected and repelled in no time.
On the one hand, this is based on an even more comprehensive data base, which is created by evaluating additional metadata. The above examples provide an outlook on what will be possible in the future by correlating metadata. On the other hand, the 32Guards project is continuously equipped with new capabilities. Just one example: In the future, it will be possible to evaluate the contents of archives in real time and thus to recognize what is hidden in the respective archive.
Start project 32Guards now
Interested customers can now unlock the beta version of Projekt 32Guards. After activation, your NoSpamProxy installation will receive a classification of the requested data, potentially improving the existing spam protection with NoSpamProxy. All data that NoSpamProxy instances exchange via 32Guards is largely anonymized. However, file names or link names may also contain personal data or references to sensitive topics. A link with the complete list of data exchanged by 32Guards can be found in the documentation.
To use the beta version of Project 32Guards, send an email with the subject “32Guards Unlock” to NoSpamProxy support and attach a screenshot of your license details.