How are the attacks carried out?
The criminals use a prepared ActiveX element as an attack vector, which they insert into Microsoft Word files. After opening the file, malicious code is then downloaded via the browser and infects the respective computer. In the cases observed, Cobalt Strike was loaded first, which is also used for threats from dangerous XLL files.
The vulnerability lies in the browser engine MSHTML (also called Trident), which enables the reloading mentioned. This engine is the HTML rendering engine of all versions of Internet Explorer on Windows systems. It was introduced with Internet Explorer 4 and is a core component of all versions of the browser.
It is also possible that users of other browsers are affected by the vulnerability.
What does Microsoft say?
The vulnerability can be viewed at Microsoft under the number CVE-2021-40444. As mentioned on the page, the vulnerability is already being actively exploited. Microsoft points out that no elevated rights or special requirements are necessary to carry out the attack.
How can you protect yourself?
NoSpamProxy protects through Content Disarm and Reconstruction (CDR)
NoSpamProxy users can protect themselves from dangerous docx files by configuring Content Disarm and Reconstruction (CDR) in a content filter action accordingly.
- Go to Configuration > Content filter > Content filter actions and click Add.
- Create the content filter action and tick the checkbox Convert Word documents into PDF on the Content Disarm page.
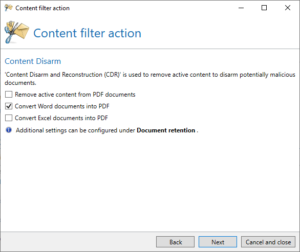
- Make the further settings as required.
- Select the content filter action in the corresponding content filter entry.
You are now protected by CDR.
Be aware that the process of converting to PDF terminates with an error message. This is a normal behaviour and not a malfunction.
Disable ActiveX via Registry
Microsoft is working on an official fix and until then recommends disabling ActiveX controls completely via the registry.
Be aware that ActiveX elements that are already active remain unaffected by this.



