What are XLL files?
XLL files are Excel macro libraries and belong to the category of Excel add-ins. In newer Excel versions they have been replaced by XLAM files. Both offer the possibility to use user-defined functionalities in Microsoft Excel.
Why are XLL files dangerous?
XLLs are dynamic link libraries (DLLs) and therefore executable files. Many people know that you should not download every .exe file – but this also applies to XLL files: Like .exe files, these consist of binary code that can execute a wide variety of functions within the right host programme.
The host of an XLL file is obviously Microsoft Excel, and all files in the XLL format are automatically linked to Excel. When the user opens such a file, Excel is opened, which first asks for permission to execute the respective add-in – and thus the code it contains.
There are a variety of legitimate add-ins that can be used to extend the functionality of Excel, from calendar tools to charting to data analysis and formatting. The possibilities are almost endless – and unfortunately so are the possibilities for misuse, which the Internet Storm Center warned about as early as July 2021.
The contamination with malware Hancitor is only the first step
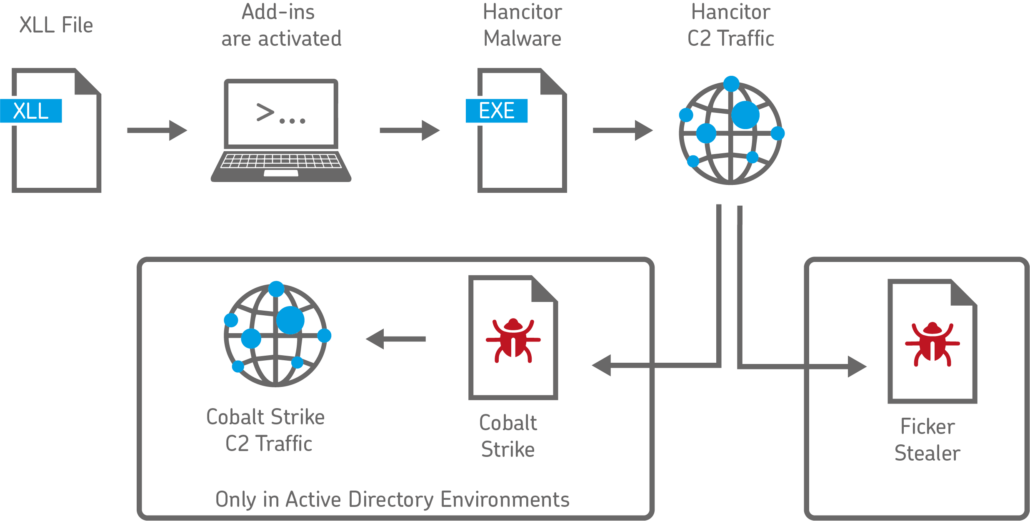
The criminals use various attack vectors to distribute the malicious XLL files. In some cases, victims are directed to fake websites using phishing emails, from which the XLL file is then downloaded, which in turn loads further malware.
Often, however, the XLL files are sent directly as an email attachment. If the default blocking of XLL files has been deactivated by the administrator, a single click is enough to set the infection of the computer in motion. The malware used in the cases observed by the Internet Storm Center is Hancitor (also known as Chanitor), which has been spreading since 2013 and in this scenario initially generates so-called command and control traffic (C2 traffic).
This means that the infected computer contacts a server that provides further instructions. In the recent past, two subsequent scenarios were observed after infection with Hancitor:
Attacks through Cobalt Strike in Active Directory Environments
Cobalt Strike is a legitimate commercial tool for penetration testing. It is used to re-enact attacks by cybercriminals in realistic scenarios to improve defences against criminals.
Unfortunately, Cobalt Strike is now often used by the criminals themselves, because they can execute practically any kind of command on the affected computers, transfer data, perform keylogging and much more. Cobalt Strike is used exclusively in Active Directory environments.
Attacks through Ficker Stealer
Since 2020, the Infostealer malware Ficker Stealer has appeared in increasing numbers. It is used by criminals to steal sensitive information of all kinds: passwords, FTP client information, login information and session information from various chat and email clients, credit card information and much more.
Example of a possible malware infection through XLL files
NoSpamProxy protects against harmful XLL files
Users of NoSpamProxy are protected twice against these dangerous files, because both our Metadata Service and the content filter recognise and block them:
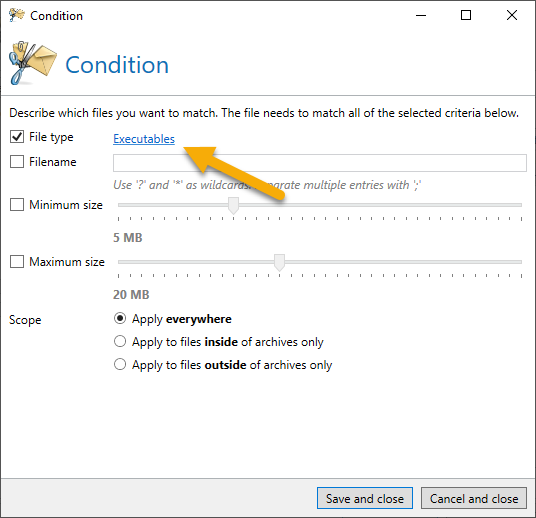
Easily sort out executable files
In the content filter, it is sufficient to define executable files as a condition in a content filter entry. The corresponding email is then either rejected or the XLL attachment is removed, depending on the configuration of the content filter:
Metadata Service adjusts the evaluation of emails
The Metadata Service also recognises XLL files and assigns 4 SCL points by default. This means that the Spam Confidence Level is adjusted accordingly, which means that the respective email is accurately recognised as a threat and sorted out.
Automatically protected with NoSpamProxy Cloud
Even in the standard configuration of NoSpamProxy Cloud, you are protected against threats from XLL files. Even without configuring the content filter yourself, XLL files are recognised and the respective emails are rejected.
Protect yourself from attacks with XLL files – test NoSpamProxy now!
With NoSpamProxy you can reliably protect your company against cyber attacks. Request your trial version now!