The Digital Strategy 2025 of the Federal Ministry of Economics and Energy (BMWi) supports medium-sized companies with regard to the increase of data security. In particular, the use of e-mail encryption with special solutions to complement the classic e-mail servers is required as a necessary measure. The “Compass for IT Encryption” emphasizes the user-friendliness of future-proof gateway-based solutions in this regard.
The General Data Protection Regulation (GDPR) aims at harmonising the handling of personal information by organisations. Numerous organisations are already working on implementing and conforming to the individual items of the GDPR. But what’s really behind the GDPR?
Oliver Schonschek, journalist specialised in IT, uncovers common myths circulating online and answers the most important questions.
Due to their architecture, numerous processors are affected by a pair of vulnerabilities, Meltdown and Spectre. The malware that exploits the two can be delivered by email. NoSpamProxy takes multiple approaches to attachment processing and blocks attachments containing malicious code reliably.
As of January 1,2018, many energy suppliers have converted the solutions they use for EDI message exchange to the encrypted communication required by the EDI@Energy Directive. Afterwards a significant proportion of incoming mails could not be decrypted by NoSpamProxy and was either rejected or not delivered.
Electronic greeting cards are becoming increasingly popular and, above all, on public holidays. The e-cards are cheap and the shipping is compared to analog Christmas cards with little effort. However, digital greeting cards are often used by attackers to transmit spam and malware. The criminals are often successful with bad attachments or links.
In the TeleTrusT Heise special supplement of the current issue of the magazine “iX” an article of Stefan Cink was published on the subject of “Security and Data Protection”. The product manager of NoSpamProxy pointed out the importance of sender reputation for a secure and efficient e-mail communication in the article “Sender you can rely on – standards for sender identification ensure greater security in e-mail traffic”.
Net at Work gave a lecture about e-mail security at the T.I.S.P. community meeting of the TeleTrust Association and provided for a successful exchange.
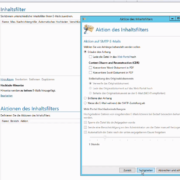
New video for setting up Content Disarming & Reconstruction (CDR) In our new video tutorial we show step by step how to set up the content filter in NoSpamProxy 12 and which new features there are.
NoSpamProxy
Categories
Latest News
 NoSpamProxy Server 15.1 now available24.04.2024 - 15:38
NoSpamProxy Server 15.1 now available24.04.2024 - 15:38 Deactivation of the knowledge base: What you need to do now23.04.2024 - 10:00
Deactivation of the knowledge base: What you need to do now23.04.2024 - 10:00