What is 32Guards?
The 32Guards action in NoSpamProxy collects and analyses metadata about emails and attachments. The goal is to build an even more powerful anti-malware intelligence that can detect and defend against spam and malware attacks even faster and more accurately.
32Guards filters out dangerous URLs from phishing emails
With the introduction of a web crawling service, 32Guards is now able to collect even more meaningful data regarding URL redirects, distinguishing dangerous links from harmless ones.
In its current state, this service has two main uses. First, URL redirects can be resolved, and second, hashes and mimetypes of file downloads can be determined. The focus of this article is on URL redirects. Of course, randomly checking URLs for redirects is not a good idea for several reasons, one of them being the fact that the cost would be disproportionate to the usefulness of the information gathered when 50 million URLs are seen each week and may need to be checked multiple times.
The following figure shows an overview of the pages examined:
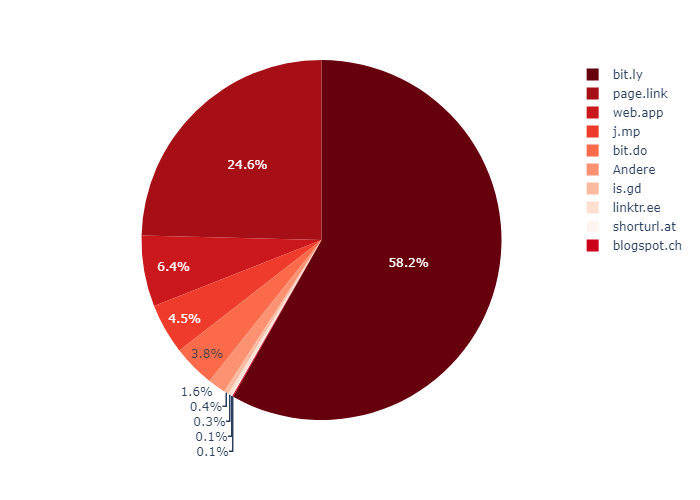
Bit.ly links make up the largest part here. Various subdomains on Google Firebase (page.link) are also among the frequently sighted (and crawled) URLs. Rather rarely, but still significantly, links to other URL shortener services such as “j.mp” and “is.gd” are spotted.
Short URLs tend to lead to phishing pages
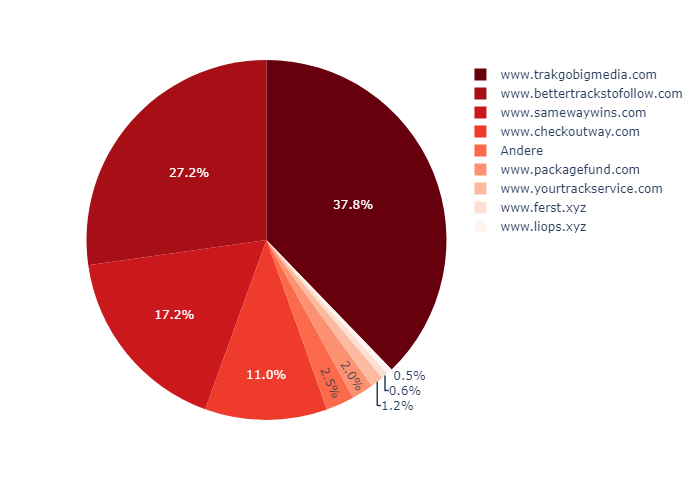
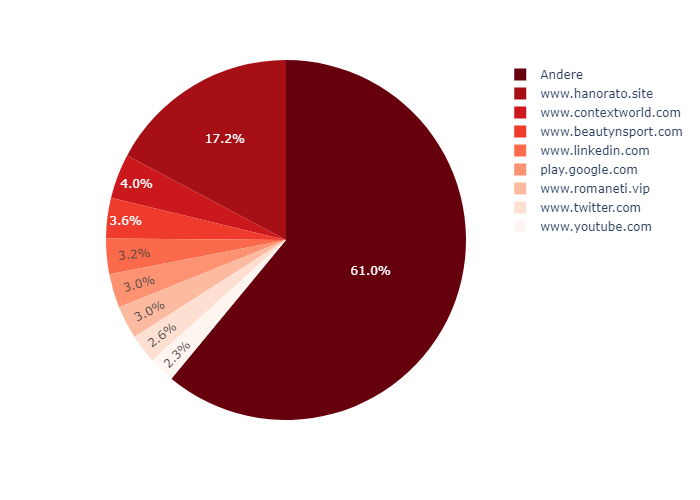
It is noticeable that a significant proportion of the URLs examined lead to known phishing or spam pages, which are known to VirusTotal, for example. Thematically, a number of topics areas are covered. Most of the domain names speak for themselves. Such a distribution can also be determined in relation to individual services.
The bit.ly links forward to a large number of different domains, as is to be expected. For this reason, the category “Other” also dominates. Here, the sightings of all less frequently seen target domains are summarized. Otherwise, both malicious sites and links to reputable sites can be found here. Nevertheless, it can be assumed that the malicious links dominate.
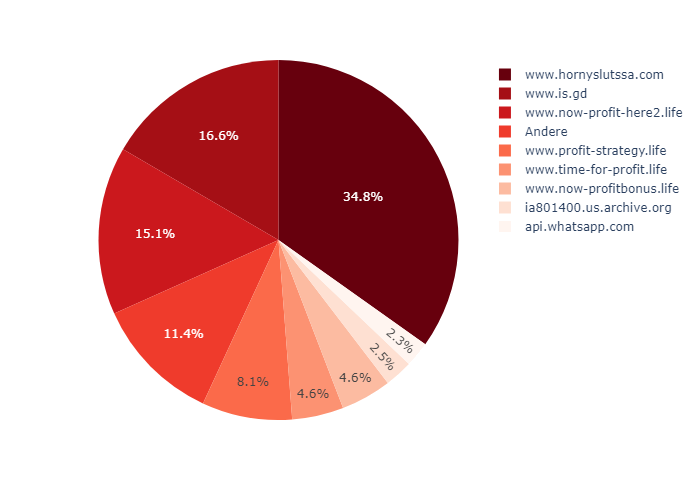
The picture is different for smaller URL shortener services such as “is.gd”. Here, redirects to malicious or at least undesirable pages are found to a predominant extent.
The images in the following gallery provide an overview of the link targets, both in general and limited to bit.ly and is.gd, respectively:
Forwarding chains indicate phishing
Another criterion for the evaluation is the type of forwarding. It makes a big difference whether the short link leads directly to the desired destination or whether there is a chain of redirects. The crawler service determines the length of this chain as well as all intermediate URLs.
In most cases, the target is reached directly or with an intermediate step. However, up to nine intermediate stops may be made – not a good sign. Characters. The graphs below show the length distribution of these forwarding chains, as well as the destination domains of chains longer than four. This data also supports the thesis that long forwarding chains often lead to malicious pages.
Web crawling with 32Guards increases protection against dangerous short URLs
All in all, it turns out that web crawling can be used to generate helpful and interesting data. For example, specific short links can be evaluated and then included as Indicators of Compromise (IOCs). Important IOCs are shortener URLs already known to be suspicious, the fact that short URLs often point to the same destination, or long forwarding chains. In addition, entire services such as is.gd or subdomains such as klow.page.link can also be assessed and assigned SCL points with pinpoint accuracy. This significantly improves protection against phishing emails.
However, the possibilities go even further: by determining the URLs behind the short links, suspicious URLs can also be found and evaluated before they appear “unveiled” in emails. This, in turn, helps 32Guards to continuously improve its performance with regard to URLs detected for the first time.
Basically, it remains to be said that nothing good is hidden behind most short links. In any case, 32Guards offers fast and proactive protection by detecting dangerous and fraudulent links as well as the underlying patterns and protecting you and your company from malware, ransomware and spam. Detecting patterns as well as correlating the results of the investigation with meta-data collected by 32Guards enables real-time assessment of the collected data and a continuously increasing level of protection for your company.
Use 32Guards now
The 32Guards action in NoSpamProxy ensures that metadata on emails and attachments is collected and analyzed. The goal: to build an even more powerful anti-malware intelligence made in Germany that can detect and defend against spam and malware attacks even faster and more accurately. If you are interested in using the beta version of Project 32Guards, send an email with the subject “32Guards activation” to NoSpamProxy support and attach a screenshot of your license details.