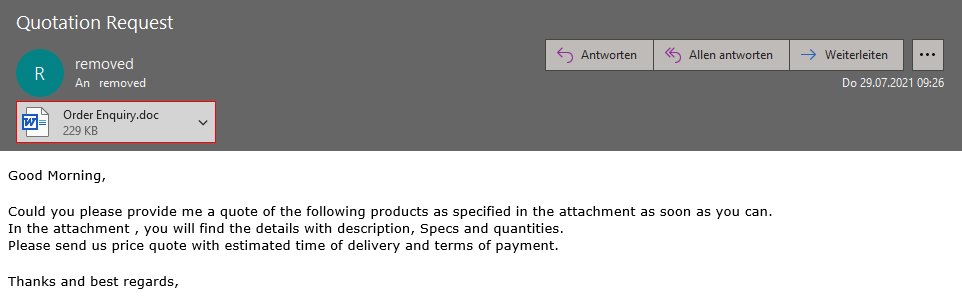
Example of a recent spam message with a malicious RTF document.
At first glance, the attachment looks like a Word document. This simple trick has long been used in the repertoire of spammers, because unfortunately Microsoft Word is so forgiving and also opens these documents. In our blog blog, we already recommended actions in 2018 in the wake of Emotet to successfully fend off a corresponding mismatch of the file type and file extension in the content filter.
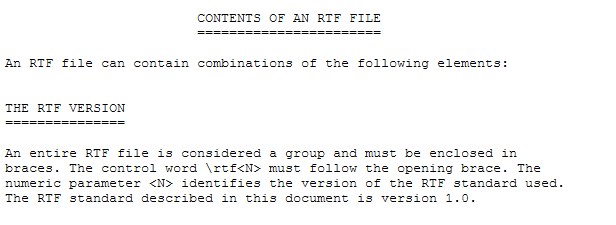
In the current wave, the header of the RTF document is now also additionally manipulated. In the original rich text specification from June 1992, Microsoft defines the header as follows:
The first rich text specification appeared 29 years ago.
But in Redmond they don’t seem to stick to their own specification and spammers now use documents which don’t start with “{rtf1”. Unfortunately, Microsoft Word is also so tolerant here and opens the manipulated RTF documents, which e.g. only begin with “{rt”.
Due to these manipulations of the RTF header the file type detection in NoSpamProxy does not work correctly anymore and the attachment is falsely detected as “Text only / Plain text”.
Various test documents and detection in NoSpamProxy Message Tracking
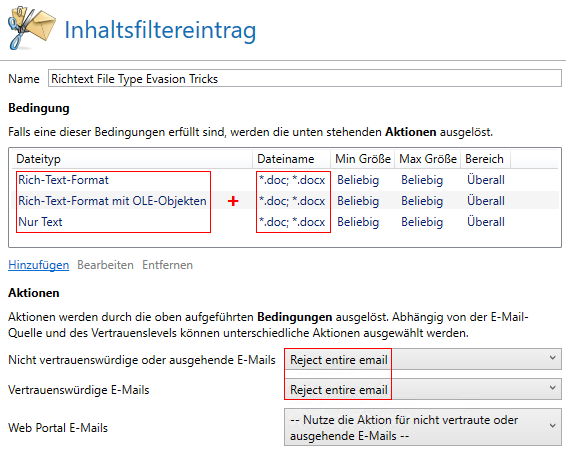
Configure content filter
For stricter handling of these spam emails, we recommend the following temporary local modification:
Therefore, configure the content filter entry as described in “Configuration option 2” of the Knowledge Base article “Configuring content filters“.
- File type: Text -> „Rich-Text-Format“ AND Filename: *.doc; *.docx
- File type: Text -> „Rich-Text-Format with OLE-Objects“ AND Filename: *.doc; *.docx
- File type: Text -> „Only Text“ AND Filename: *.doc; *.docx
SQL query
Furthermore, we provide an SQL query to search for such tricks on RTF documents in the NoSpamProxy database: Download
Here you can also quickly see in advance whether this tightening in the content filter could possibly lead to problems with legitimate e-mails from partners. This gives you the opportunity to address these affected partners and point out the upcoming tightening of your e-mail policy in advance.
- Install Microsoft SQL Management Studio on the system where the affected database is installed. Microsoft SQL Management Studio is available free of charge on the Microsoft website.
- Start the SQL Management Studio.
- Log on to the SQL instance where the database is running. Usually these instances are called (local)SQLEXPRESS or (local)NOSPAMPROXY.
- After successful login, execute the SQL query
Test documents
We also provide the following harmless “Hello World” test documents to be able to test the successful tightening in the content filter as well:
IOC List
Filename: „Order Enquiry.doc“
Sha256 Hash: 83d493530df0cc487e1adf6684ffef73415f69d54c0b665d7276d81575f2dc02