Email encryption with PGP
PGP stands for Pretty Good Privacy and was actually a software for email encryption developed by Phil Zimmermann in 1991. Nowadays, however, the term PGP is used synonymously for the encryption method used.
Since PGP belongs to the hybrid cryptosystems, two different types of keys are required for its use:
Public key
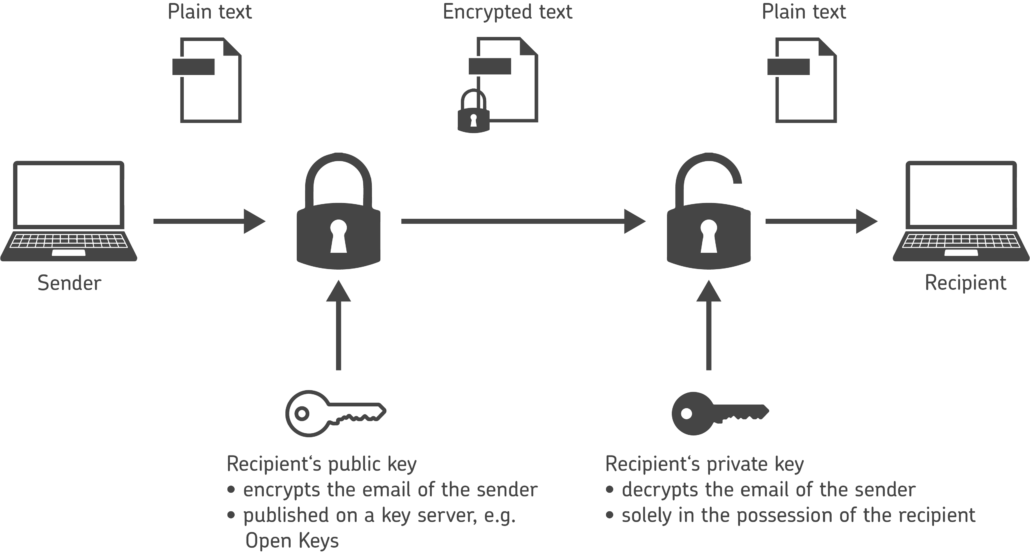
The public key is in the possession of the sender. With this key, the senders can encrypt data and verify signatures.
Private key
A private (secret) key that is exclusively in the possession of the recipient. This key is used for decryption.
In order to use PGP encryption, the sender must have his private key and the public keys of all recipients. Both keys can be generated with appropriate software.
How does PGP encryption work?
The sender uses the public key of the subsequent recipient to encrypt emails to that recipient. Beforehand, the recipient must have distributed this public key – whether by email, on a website or via a free key server such as Open Keys. Since only the recipient has the matching private key, only the recipient can decrypt the email.
Up to this point, this encryption system would be called asymmetric, because two different types of keys are used. With PGP Mail, however, we speak of hybrid encryption because the plaintext message is symmetrically encrypted with a randomly generated session key, which is then asymmetrically encrypted with the recipient’s public key and prefixed to the encrypted message.
Here, public and private keys act like padlock and key: The recipient makes his lock available to all communication partners – namely the public key. Decryption is only possible with the private key in his possession.
Ensuring integrity and authenticity with PGP Mail
With PGP, you can not only encrypt emails and thus ensure the integrity of the message. You can also sign the email and thus prove to the recipient that the email actually comes from you and has not been manipulated. In other words, that the email is authentic.
To do this, a hash value is generated from the plain text of the email by applying a cryptographic hash function – i.e. an algorithm. A signature is then generated from the resulting fingerprint with the help of the sender’s private key. The recipient can then check this signature in turn with the help of the public key.
The public keys can then be signed by other key holders, thus authenticating both the key and the user ID contained in the key. In contrast to S/MIME-based signing, this is not a hierarchical system, but a Web of Trust.
A Web of Distrust?
This Web of Trust has been subject to great criticism for some time, so much so that some are already predicting its death. However, the problems described arise primarily from the fact that non-verifying keyservers are used to upload public keys and distribute them in this way.
In such a scenario, widespread abuse is indeed possible, because theoretically anyone can upload a public key for any person to such a server. If such keys are imported, one’s own PGP installation may be paralysed. This kind of signature spam can already be called a DoS attack. In addition, it can happen that users who do not use PGP at all are suddenly bombarded with PGP-encrypted emails. A small DoS attack, so to speak.
Open Keys validates public keys
Key servers such as Open Keys validate the recipient’s address and access to the private part, as the confirmation link is in an encrypted email. Misuse is thus prevented.
And the development of PGP continues: in the Web Key Directory (WKD), keys are validated against the recipient domain using HTTPS. The system provides for setting up such a WKD on one’s own domain and storing one’s public keys there. The technology is recommended by the Federal Office for Information Security (BSI), among others.
How can I use PGP encryption easily?
Email encryption with PGP or S/MIME is important. However, many companies do not realise that PGP encryption is also easy to implement. Some fear that encryption is time-consuming and costly: private and public keys have to be managed, secured and protected. The public keys also have to be distributed. And: the users have to be trained.
The right encryption software automates all this. Outlook emails are automatically encrypted by the encryption software – the individual employee does not even realise that he or she is sending an encrypted email. Even PDFs can be encrypted in this way and sent directly as Outlook mail. The public PGP keys of your communication partners are also managed centrally and stored securely.
In this way, the encryption software also ensures that employees do not jeopardise the company’s security through carelessness or mistakes – because security policies are automatically enforced company-wide.
Protect all emails with PGP now
Whether contract details, invoices or other internal company information – every day you send emails with sensitive content to customers or partners, and countless emails travel around the world. To be sure that confidential information remains confidential on these journeys and that you always know who your counterpart is, you need powerful encryption software.