Microsoft forces secure connections to Domain Controller from March onwards
In March, Microsoft will suppress insecure connection requests to Windows domain controllers. This change was announced in August. NoSpamProxy customers can sit back and relax because they only have to check the Active Directory synchronization of NoSpamProxy – in case this hasn’t already been done. If necessary, firewall ports will have to be adjusted.
What needs to be changed in NoSpamProxy?
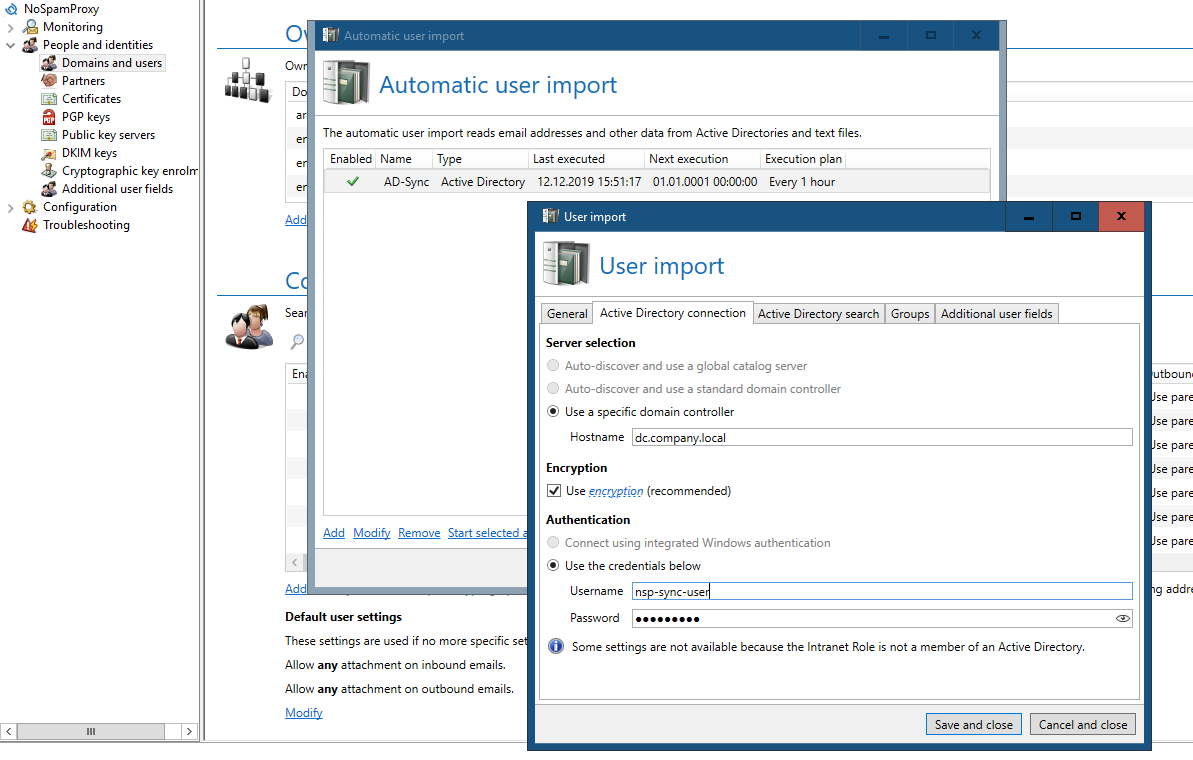
The connections to the Active Directory are maintained under People and Identities > Domains and Users. By default, the connections to the domain controller are unencrypted. To activate encryption, the checkbox “Enable encryption (recommended)” must be set in the properties of the automatic user import on the “Active Directory Connection” tab. From now on, all connections to the domain controller will be encrypted. If a firewall exists between the server with the intranet role and the domain controller, ports may have to be adapted. Please use the following table as an orientation for which ports are used with which settings:
| Server selection | Unencrypted | Encrypted |
| Auto-discover and use a global catalog server | 3268 TCP | 3269 TCP |
| Auto-discover and use a standard domain controller | 389 TCP | 636 TCP |
| Use a specific domain controller | 389 TCP | 636 TCP |
Further information on the modification
If you need more information and background on the upcoming change, please visit the Frank Carius page. On his MSXFAQ.de page you will find a comprehensive article (German only).