Remember Emotet?
Yes, exactly, the group of malware that, among other things, made companies, healthcare institutions, public authorities and other public institutions the victims of cyber attacks in 2019, in addition to countless private individuals: the Berlin Court of Appeal, the administration of the city of Frankfurt am Main, the University of Giessen, the Catholic University of Applied Sciences in Freiburg or the Fürth Clinic still think back to these attacks and their catastrophic consequences with horror. Although the Emotet infrastructure was smashed by an international action at the beginning of 2020, the “most dangerous malware in the world” recently resurfaced.
Old tricks, still dangerous
What made Emotet so successful back then was the fact that it was spread via authentic-looking emails that often followed up on emails sent shortly before – so-called “email reply chain attacks”. In many cases, the senders of the emails were, at first glance, known contacts with whom there had been a recent communication relationship. The recipient, salutation and signature also appeared authentic.
This was possible because Emotet had evaluated Outlook address books, MAPI interfaces and Active Directories of communication partners and used this information for attacks. After infecting a computer with Emotet, further malware was always loaded, including the banking Trojan Trickbot or the ransomware Ryuk.
Even more dangerous thanks to compromised Exchange servers
The supposed reply emails written by the criminals then contain links through which the malware lands on the victims’ computers. What makes this new wave of attacks so dangerous is the fact that to send the fake emails, the respective communication partners’ own legitimate email servers are misused – in the present cases Exchange servers that have been infected in advance and can now obviously be controlled by the criminals. IKEA has also just become a victim of such an attack.
A colourful bouquet of malware
As far as distributed malware is concerned, the criminals are broadly positioned: In addition to Qakbot (also known as Pinkslipbot or QBot), the distributed malware variants also include DanaBot and SquirrelWaffle. As with Emotet, the goal of the attacks is to extort a ransom for encrypted data or locked computers.
Possible effects of an attack
The German Federal Office for Information Security (BSI) provides an overview of the possible effects of such an attack in its official security warning:
It should be added that a data leak does not have to occur only after the installation of malware: Since the communication has already been read, it is possible that the information contained in the exchanged emails has already been leaked.
Why are these attacks so dangerous?
An effective way to detect fake sender domains and addresses and prevent such and other attacks are the sender reputation check procedures. These are easy to implement and make it possible to secure IT infrastructures – usually: Because the legitimate but compromised Exchange servers of the communication partners originate, the checks of SPF, DKIM, DMARC and DANE turn out positive despite malicious email content.
Even evaluation mechanisms such as Level of Trust cannot unfold their full protective effect in some cases, because the trust evaluation is also undermined by the origin of the dangerous emails. This can also be the case if third-party analysis tools have identified the respective emails as a threat.
How NoSpamProxy can protect you
As always, when it comes to protecting against cyber-attacks, potentially affected systems need to be patched. However, despite applying the latest patches, there may still be danger if the system has already been compromised before the application. The BSI recommends rebuilding the server if a compromise is suspected.
NoSpamProxy can also provide effective protection against the attacks by adjusting the configuration. Below are three tips that you can use to significantly improve the security of your organisation:
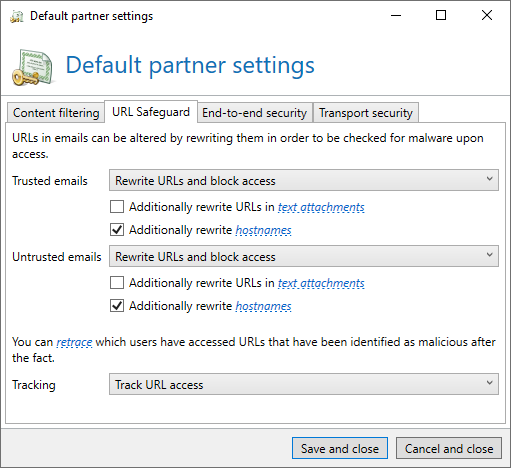
Adjusting URL Safeguard settings
The malicious links contained in the emails often do not specify the network protocol, lacking the HTTPS:// at the beginning of the URL. Instead, many links can be found that look like bulleted lists:
1) mail.example.com/maliciouslink/dontclick-28604
**) mail.example.com/maliciouslink/dontclick-286042
These URLs are not rewritten by URL Safeguard by default. Similarly, no tracking takes place.
To enable this, you must activate the rewriting of host names for trusted and untrusted emails in the default settings for partners. Once this is done, such dangerous links are redirected to the Web Portal. At the same time, it is checked whether the URL is known to be malicious.
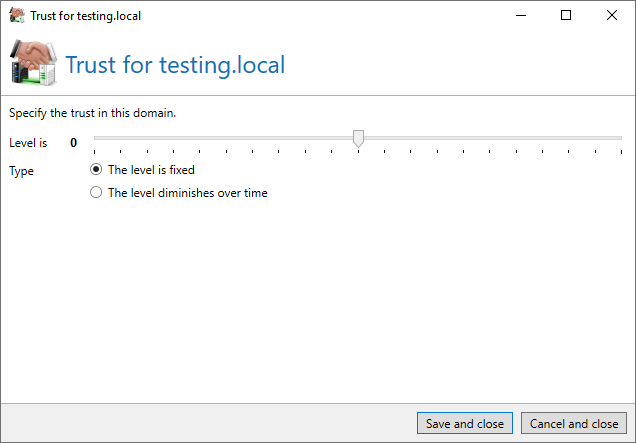
Setting appropriate trust values for partners
If you notice that one of your communication partners is sending contaminated emails via their infrastructure, set the domain trust for Level of Trust to 0 (fixed). Leave this setting until the partner has corrected the problems.
If you want to be on the safe side, you also have the option of creating a rule that generally rejects emails from this partner.
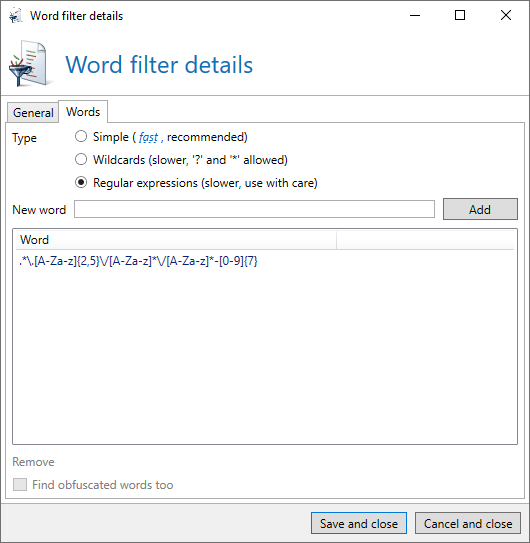
Defining a regular expression in the word filter
The filter shown covers the current attack patterns via the regular expression .*\.[A-Za-z]{2,5}\/[A-Za-z]*\/[A-Za-z]*-[0-9]{7}. Of course, this is only effective until the attackers change the patterns.
Not yet using NoSpamProxy?
With NoSpamProxy you can reliably protect your company against cyber attacks. Request your free trial version now!