Emotional people are faster at clicking dangerous phishing links
This is accompanied by a noticeable dissatisfaction in the population, which sometimes causes annoyed shrugs, sometimes a literally unhealthy tendency to adopt conspiracy theories. To a certain degree this is understandable, because with the amount of information circulating, the uncertainty is great. Unfortunately there is also a lot of false information circulating, so it is not surprising that cyber criminals also try to take advantage of the tense and emotionalised situation and get potential victims to click rashly.
With the help of the 32Guards service, the NoSpamProxy experts have been collecting metadata of the email traffic of participating NoSpamProxy customers for over a year. The 32Guards service already offers all NoSpamProxy beta participants proactive protection against phishing emails. Although the collected data consists only of essential metadata, it can be used to derive interesting insights into the threat situation and the methods used by cybercriminals to exploit the coronavirus situation for their own purposes.
Phishing links as attack vector
Phishing links are among the most important attack vectors for cybercriminals. In order to increase the probability of these malicious links being clicked, attackers like to rely on current trends when choosing the domains they use. Currently, the thematic field of Covid-19 is extremely popular here. A frequently used strategy here is to register domains that contain corona-related terms.
An investigation of the 32Guards data regarding domains from the Covid-19 complex of topics provides interesting results. Let us first look at all domains reported to 32Guards that contain at least one of the four words corona, mask(s), virus, or covid. The following figure shows the sightings of domains with these keywords over time.
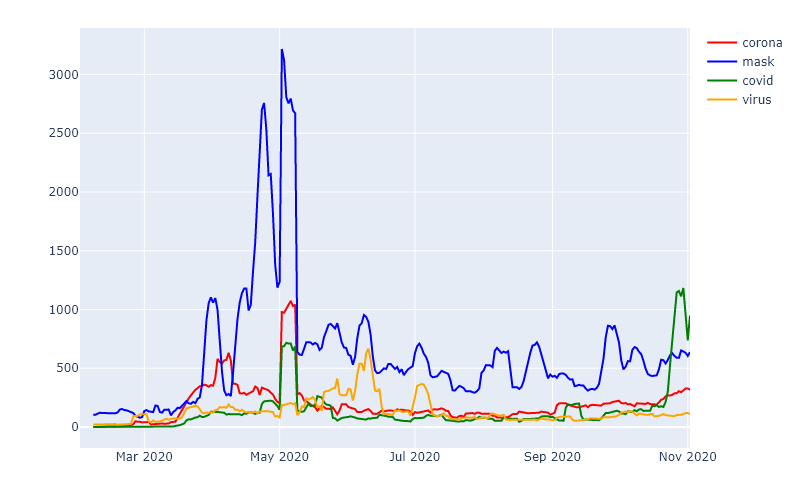
What is striking is that in the period of the “first wave” (March/April) a strongly increased occurrence was noticeable. This is true for all keywords, although the topic mask(s) was the most popular. Here, especially in the early phase, when the availability of masks was limited, fraudulent online stores were advertised.
Over the summer, similar to the infection numbers, the sighting figures stabilised at a low level. However, in contrast to the infection numbers, there was no renewed increase in the October weeks. It is important to stress here that not all sightings can be traced back to malicious domains, as many legitimate websites – such as information services – were also created during the period under review.
32Guards identifies newly created domains
In addition to the number of sightings of certain domains, it is particularly interesting to see how many completely new domains 32Guards currently recognises. Since 32Guards evaluates the information of now 250,000 users, one can assume that a majority of the domains newly sighted by 32Guards have only just been created, so-called zero-hour domains.
As mentioned above, the Covid 19 pandemic also led to some new registrations of legitimate domains. The following figure shows three examples:
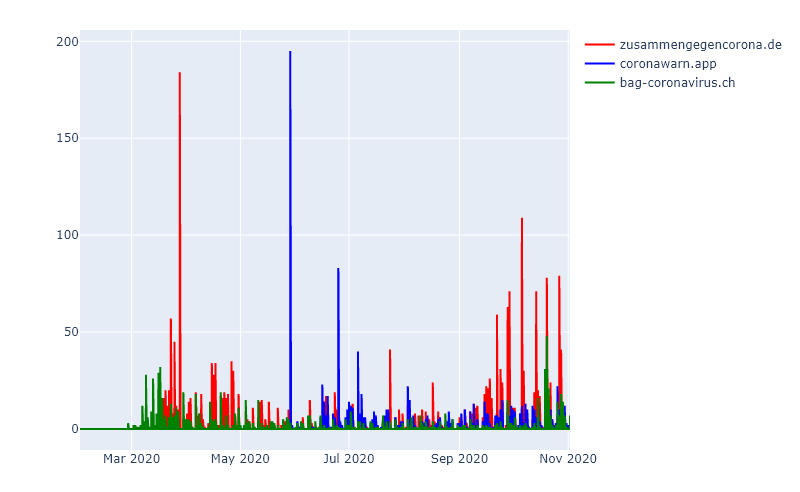
With increasing awareness of the topic Corona by the public in March and April 2020, the number of sightings of “zusammengegencorona.de”, the offer of the Federal Ministry of Health in Germany, is also increasing. The subsequent flattening and constant, but low sighting rate corresponds to the typical pattern of a legitimate domain, as does the fact that “zusammengegencorona.de” is currently being increasingly sighted again in correlation with rising infection numbers in Germany (as of November 2020).
The same can be said for “coronawarn.app”, whose sightings suddenly increase in parallel with the publication of the corresponding app, then flatten out and settle at a low level. The current increase can probably also be explained by the renewed rise in the number of infections in Germany.
In summary, it can be said that (legitimate) information offers are emerging, whose links are regularly distributed over days and weeks after an initially strong increase. Most of these links also have reputable top-level domains (TLDs) such as .de, .ch or, with some exceptions, .com.
Unusual top-level domains as a characteristic of phishing mails
If we take a look at the domains classified by 32Guards as suspicious to malicious in the early stages of the pandemic, the picture is quite different:
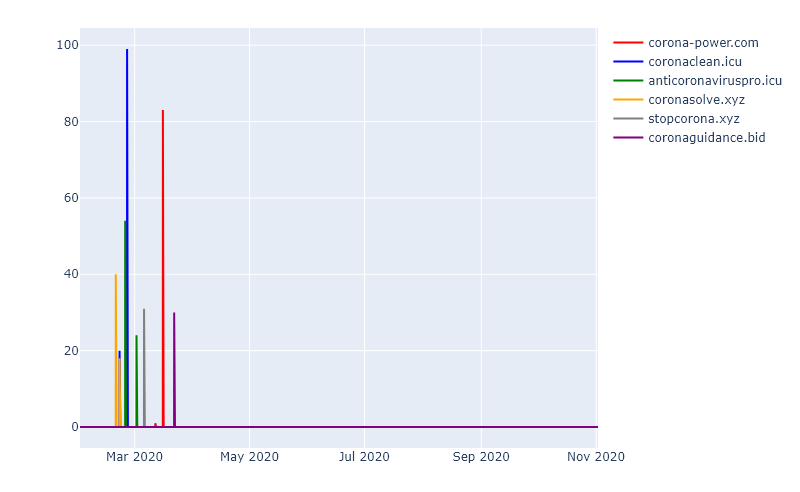
Most domains make use of rather unusual TLDs, whereby the TLD “.com” plays a special role in this picture: It does not allow a strong statement about the legitimacy of a domain, as it is not unusual for both serious and malicious websites.
In general, it can be seen that malicious domains are usually distributed in short waves. This makes it very difficult to protect against this type of phishing attack, for example. The strength of 32Guards is to quickly detect such attacks and to intervene immediately.
Cyber criminals bait Corona conspiracy theorists
We have already mentioned above that cyber criminals target their attacks on emotionalised people. The next figure shows the number of sightings of domains containing the term “mask” or “mask”.
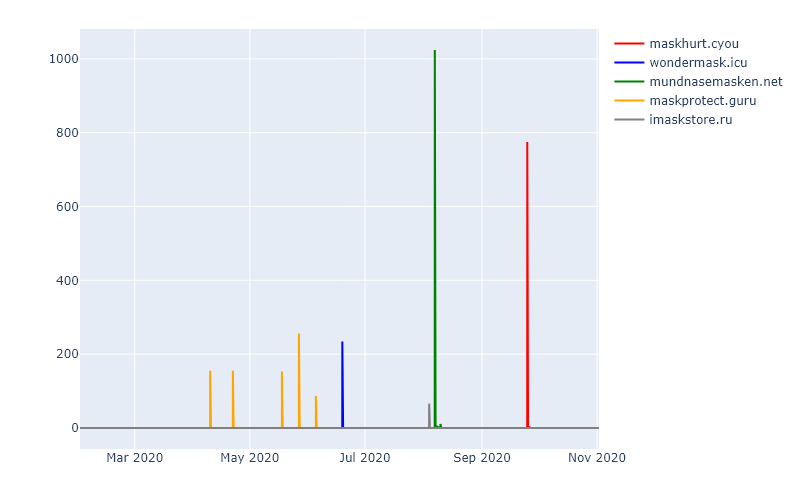
Especially the domains “maskhurt.cyou” and “mundnasemasken.net” are striking. The former is obviously intended to establish a connection to the assumed health hazards of a mouth and nose protection. The other sighted domains also take up the topic and are a way for attackers to exploit the fears of potential victims.
A look at the two previous charts also shows that the thematic focus and thus the “target group” of the attacks has changed in the course of the pandemic: While in the early phase of the pandemic, there was a tendency to try to make money through fake stores, the current situation is more conspiracy-theoretical domains in the context of “masks”.
32Guards offers proactive protection against phishing and malware
The swarm intelligence, which as the basis of 32Guards evaluates the metadata of thousands of users, is constantly growing. Cyber attacks are thus being detected faster and more unerringly. An example of this is the following pattern, which contains the term “vaccination” in different variations as part of the domain.
| nTotal | nMalware | |
| corona-impfstoff.shop | 4.0 | 0.0 |
| corona-impfstoff.store | 4.0 | 0.0 |
| corona-impfung.eu | 8.0 | 0.0 |
| corona-impfung.shop | 5.0 | 0.0 |
| corona-impfung.store | 5.0 | 0.0 |
In all the cases shown, a fast and proactive approach was able to protect against malware and fend off malicious emails.
Email attachments also spread malware
A second attack vector besides links contained in emails are attachments. Here, too, 32Guards collects corresponding metadata, such as the type of email attachments or the name of the corresponding attachment. Of course, the keyword “Corona” has also been a frequent occurrence here in recent weeks. The good news is that most of this communication is trustworthy. However, the security experts at NoSpamProxy have also recorded over a hundred cases in which attempts have been made to exploit the current situation to distribute malware. Here are a few examples:
- Use of outdated archive formats. The archive formats can still be opened using 7zip, for example, but often slip through “usual” security checks. In this case, for example, several attachments named “solution_to_coronavirus.ace” were sighted containing malware.
- Camouflage of executable file formats as PDF. This is achieved by using the .pdf extension within the file name. For example, 32Guards was able to view an attachment named “corona_treatment,pdf.iso” over fifty times, which uses exactly this trick.
Here is an example of an email whose attachment contains a _pdf as part of the file name, although it is actually a rar archive:

Conclusion
The examples shown reveal the usual attempts by cyber criminals to exploit the uncertainty of potential victims and to base their actions on current social trends and issues. There are always quick clickers, but a pandemic and the fears and worries in the population associated with it cause many to act thoughtlessly and fall for fraudulent links.
The 32Guards service provides fast and proactive protection by detecting dangerous and fraudulent links and their underlying patterns and protecting you and your business from malware, ransomware and spam.
Use 32Guards now
The 32Guards action in NoSpamProxy collects and analyses metadata about emails and attachments. The goal: to build an even more powerful anti-malware intelligence that can detect and fend off attacks by spam and malware even faster and more purposefully. If you are interested in using the beta version of 32Guards, send an email with the subject “32Guards activation” to NoSpamProxy support and attach a screenshot of your license details.



