Is Sandboxing a Miracle Cure or a Hype?
IT infrastructures today are regularly exposed to dangerous and sophisticated attacks by hackers. With the growing number of attacks, the technological maturity of the attack methods used increases: Emotet, WannaCry, Locky, DDOS attacks or Zip bombs repeatedly threaten companies and authorities, and in many cases cause considerable damage.
According to the Federal Office for Information Security in Germany, two-thirds of German companies and authorities were victims of hacker attacks in 2016 and 2017, and one-quarter of these cyber attacks led to operational failures.* This is not just about losing the ability to act or financial losses, but also about the loss and misuse of confidential data.
Conventional protective mechanisms are no longer sufficient
Effective anti-spam software, email gateways and firewalls are now part of the basic configuration of every proper IT landscape. The attackers, however, equip themselves and find security gaps or loopholes at regular intervals through which they place malware on the victim’s computers or networks.
Manufacturers of anti-spam and anti-malware software are making corresponding efforts to add further levels of protection to their products. The so-called Sandbox is often discussed as a particularly promising level of protection against spam and malware.
How a Sandbox works
The basic principle of sandboxing is to isolate the executed file from the system environment and thus protect it from the potentially harmful effects. In this case, it is about files that are to be scanned for malware. This works because the sandbox is separate from the system’s resources, but provides all the relevant functionality.
In the area of email security, a sandbox pretends to the links and attachments to be tested that they have been delivered, are on the client and are being opened. This detonation process, i.e the opening of the files, is then observed and evaluated. Sandboxing is therefore another layer of protection against spam and malware for email security that is primarily used to defend against zero-day attacks, targeted attacks and advanced persistent threats.
Hackers respond to the sandbox trend
However, malware developers are developing countermeasures and are now able to detect traditional sandboxing environments. In such cases, the malware aborts the execution of the malicious code; this is referred to as sandbox evasion and makes successful analysis difficult or even impossible.
In these cases, it is crucial to use effective spam filters with functions such as Content Disarm and Reconstruction (CDR), intelligent content filters, URL rewriting or the option of delayed delivery. This means that there is already basic protection that eliminates many threats and significantly reduces the number of files that are uploaded to the sandbox.
Using Sandbox Arrays to prevent Sandbox Evasion
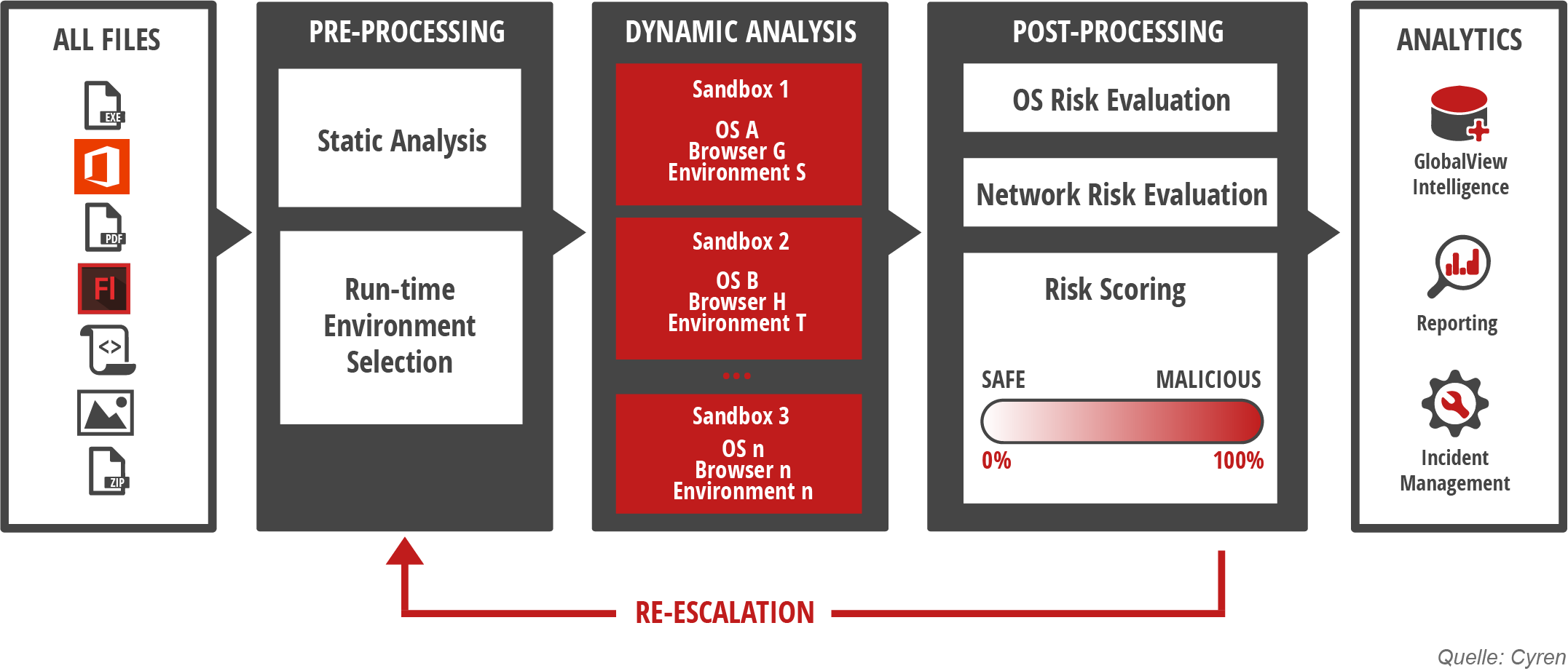
The situation is different again when not only a single sandbox, but a sandbox array – i.e. a row of sandboxes connected in series – is used. The files to be checked are checked in different sandboxes, which work on the basis of both virtual and physical computers. In order to make the checking process as efficient as possible, an expected behavior is predicted on the basis of the file type (static analysis) and an environment optimized for this prediction is started (dynamic analysis). Only if the expected behavior does not occur, further virtual computers are provisioned (post-processing). Malicious files and URLs can thus be reliably detected and the mechanisms of sandbox evasion bypassed.
NoSpamProxy Sandbox Service provides security
NoSpamProxy uses a cloud-based sandbox array technology that securely detects malicious files and URLs and quickly distributes this knowledge by means of comprehensive swarm intelligence. In addition, intelligent spam filters ensure that most threats are detected before sandboxing is required. In this way, you save time, resources, networks and infrastructure.
* Cyber Security Survey 2017 by the Federal Office for Information Security (in German only)