The threat landscape in the field of email is constantly changing, and new trends can often be observed within very short periods of time. For this reason, 32Guards analyses the metadata of now almost 40 million emails per week in real time, as this enables the early detection of these trends. All NoSpamProxy instances connected to 32Guards benefit from the insights gained and can thus take even more efficient action against spam emails.
Traditional spam comes in short waves
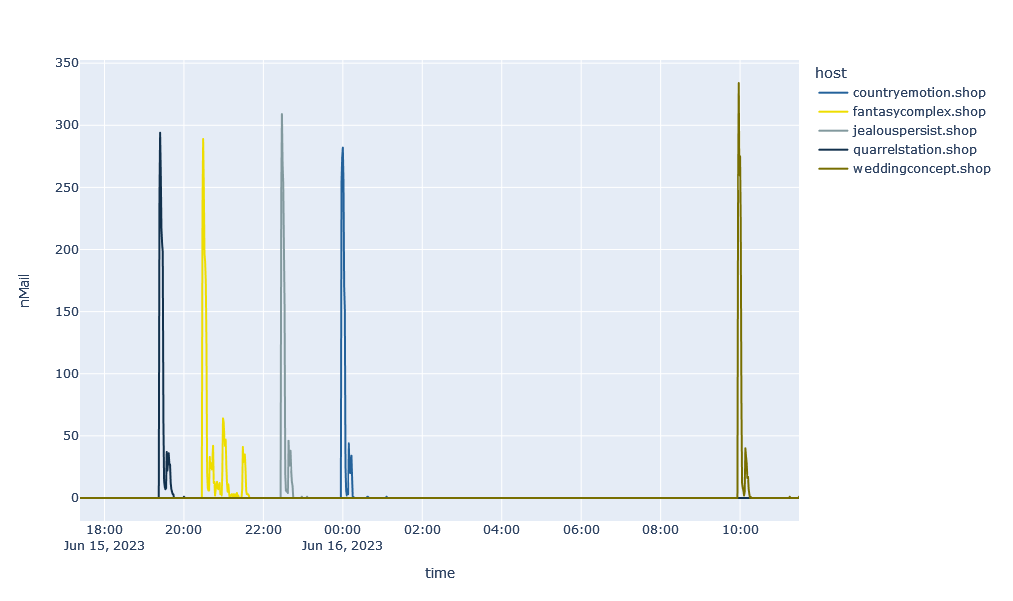
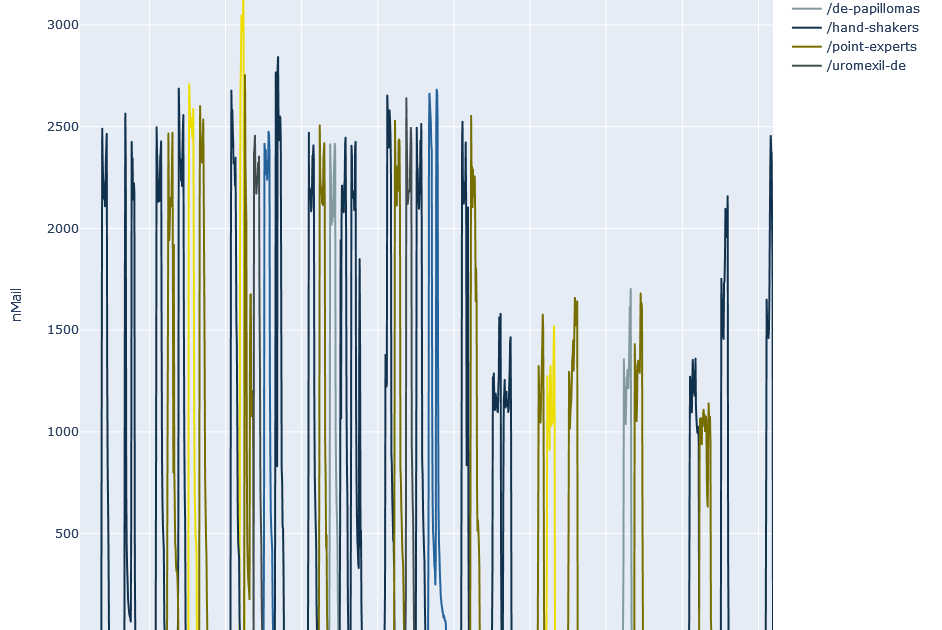
To approach the issue of Workday-Spam, it is first necessary to take a step back. Conventional spam is different from more targeted attacks such as phishing or CxO fraud attacks. The aim of these conventional spams is to lure the victim to a website, which usually contains a (fake) web shop. For this purpose, customised URLs or URL shortener links are often distributed on a large scale. Since these URLs are quite easy to recognise, the spammers often only have a short time window to distribute them. The following graph shows the sightings of selected spam URLs as a function of time:
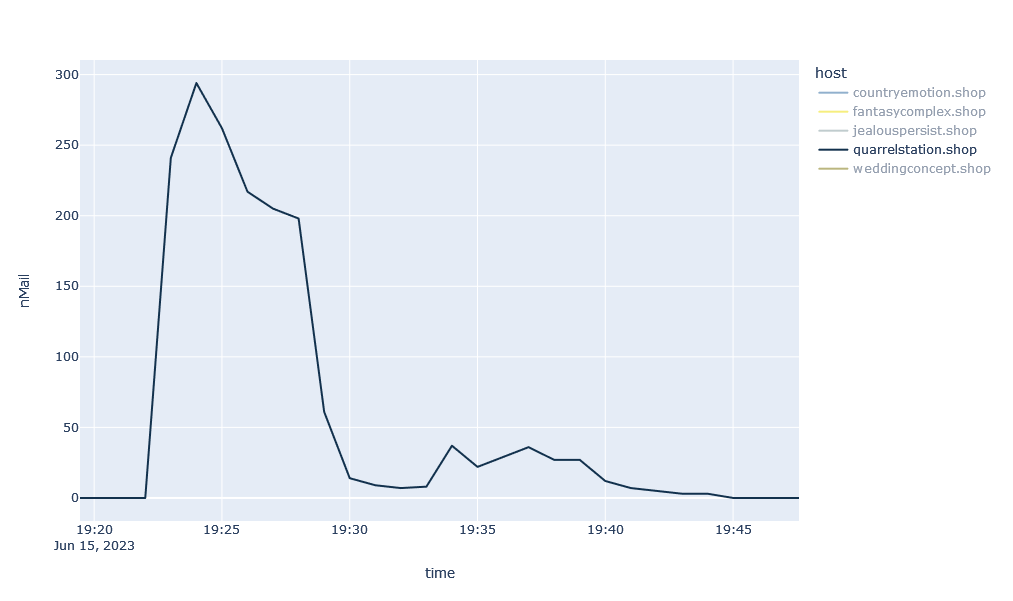
Here we see short waves that quickly come to a halt. This becomes even clearer when you look at a single wave in detail:
In the example shown here, it takes less than ten minutes for a large part of the spam wave to subside. The challenge in these cases is the speed of detection. In order to provide effective protection, such spam URLs must be detected within a few minutes. Since these patterns have been known in 32Guards for some time, fast detection is a routine task in most of these cases.
Spam with a 5-day week
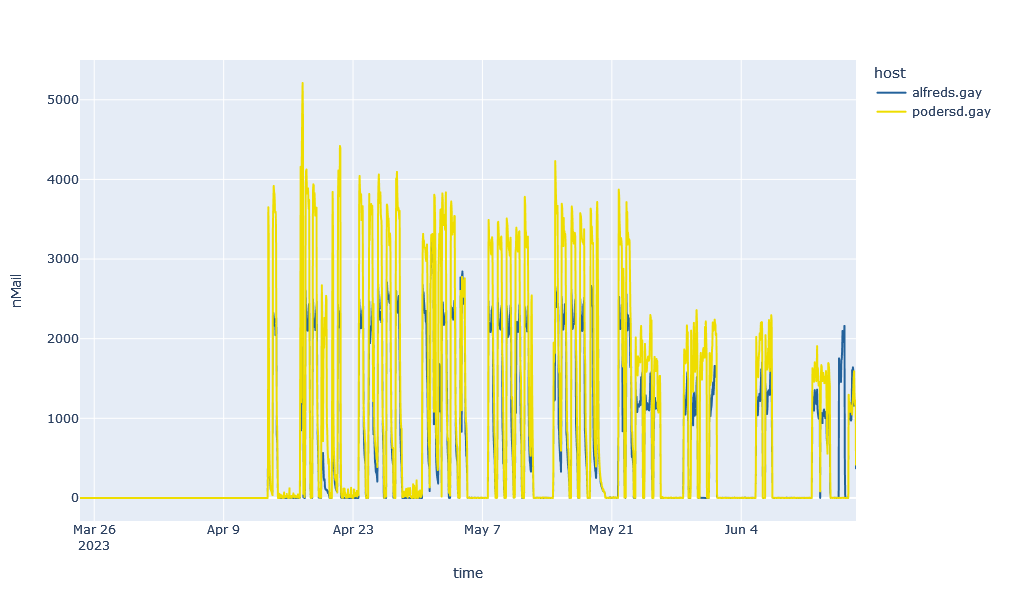
In recent months, we have observed spam URLs that are distributed according to a completely different pattern and in large quantities. Two examples are the domains alfreds.gay and podersd.gay. The following graph shows the sighting of URLs with the respective domain over time:
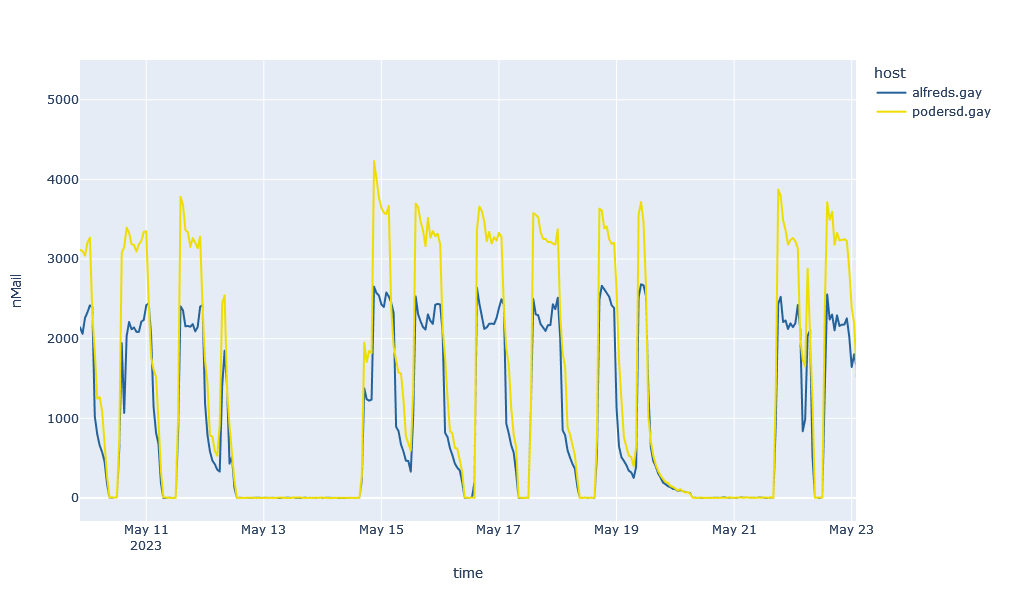
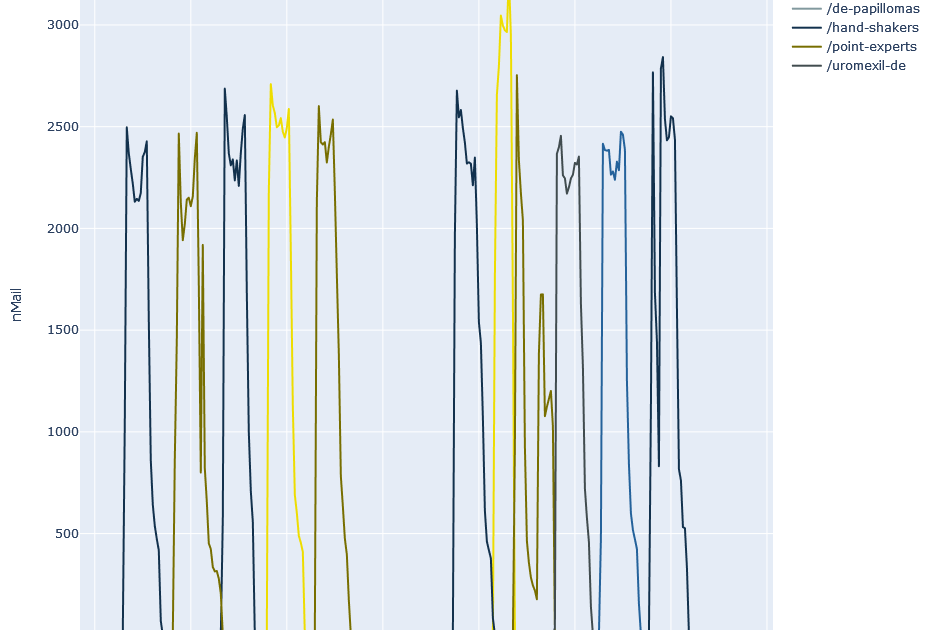
It is noticeable that there is virtually no spam with these URLs at the weekend. In addition, five distinctive peaks can already be identified here for each week ( excluding public holidays). The pattern becomes even clearer if you look at a period of two weeks:
Not only does it show that almost no spam is sighted at the weekend, but also that the spam is mainly distributed during working hours in the DACH region. This pattern is very similar to the distribution of legitimate URLs in business communication and thus more difficult to detect.
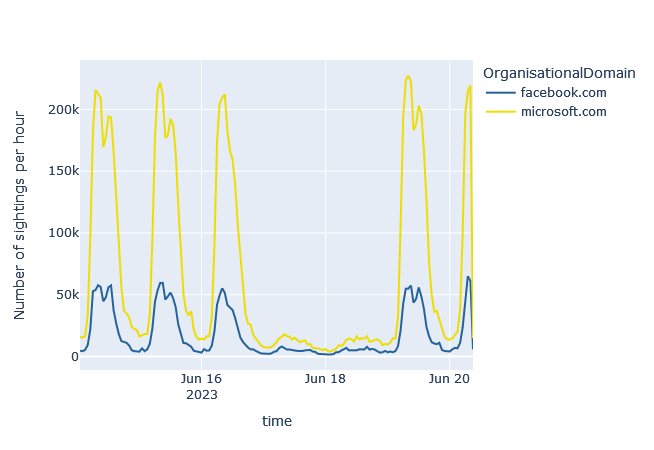
Workday-Spam uses domains for longer periods of time
Precisely because of the occurrence of these spam emails during working hours, we have named this class of spam “Workday-Spam”. It is also noticeable that the same domains are sometimes used over many weeks or months. For comparison, the following shows the weekly course of sightings of URLs for two legitimate domains. This is in stark contrast to the first example, where the domain of the URL was no longer significantly sighted after only ten minutes.
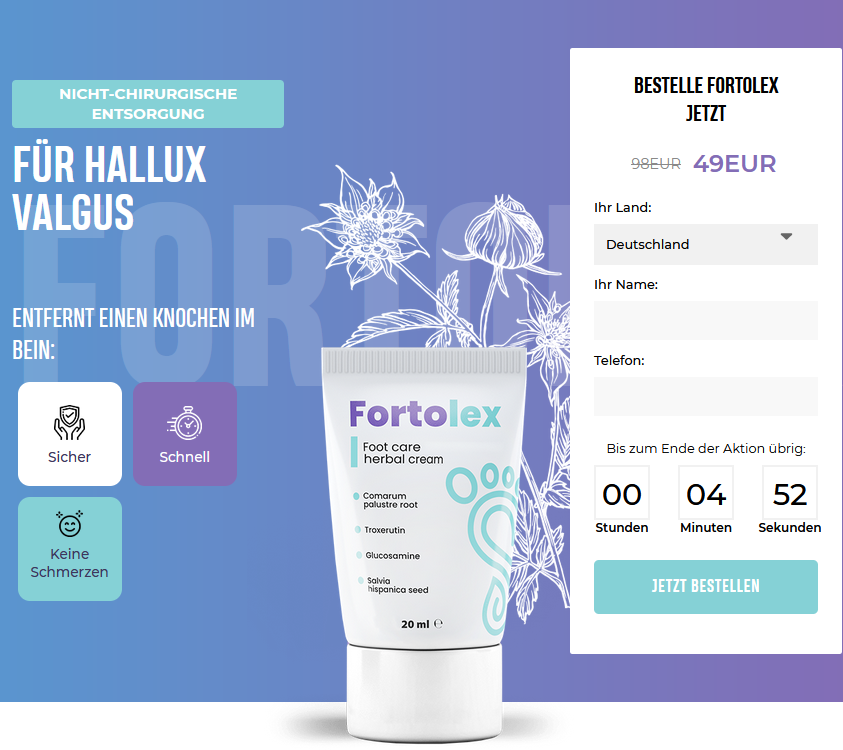
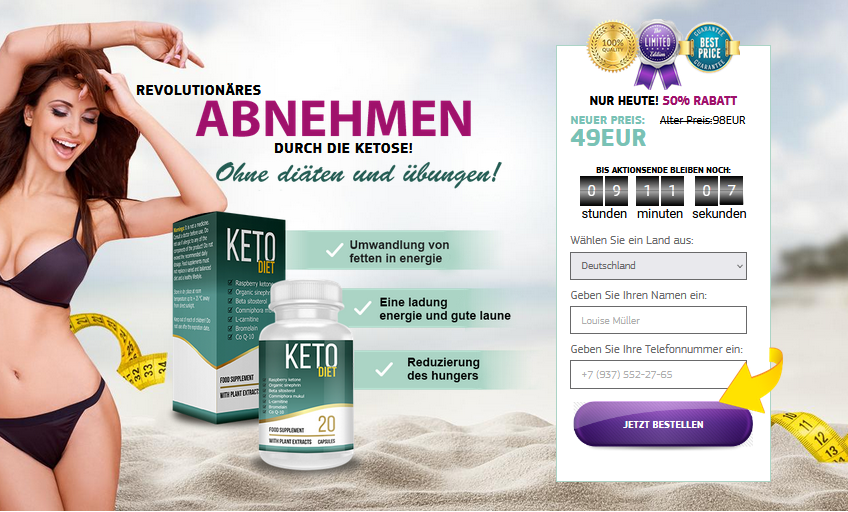
But where do these links actually lead to? In most cases, a redirect is set up on the URLs sent. These then point to various fake webshops. Below are some screenshots of these shops:
Even if the products offered differ, it is immediately noticeable that this spam is tailor-made for the German-speaking region. In addition, the shops often use conventional social engineering tricks such as promising high discounts and creating artificial time pressure by displaying counting down clocks.
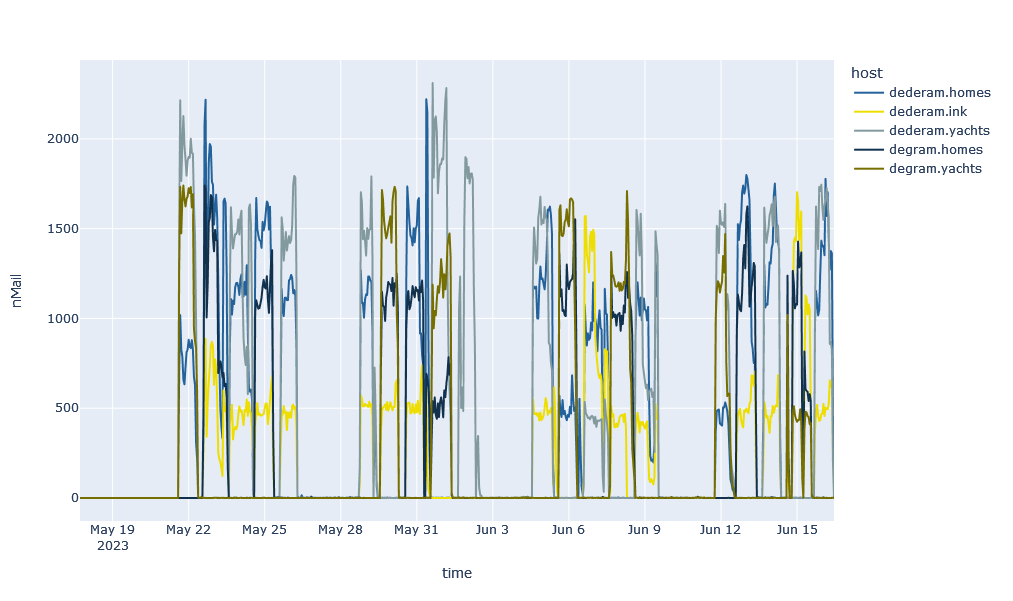
In the data collected by 32Guards, in addition to the two shown above, other domains can be found that follow the pattern of Workday-Spam. Some examples:
The domains selected here use the same names with different top-level domains (TLDs). The different domains are changed from day to day in the course of the week. In addition, a similar set of characteristic TLDs such as gay, ink, yachts and homes can also be found again and again.
Paths in Workday-Spam Point to Common Cluster
Not only do the domains of the Workday-Spam URLs fulfil a certain pattern, a look at the paths of the respective URLs also provides interesting insights. For the URLs to the domain alfreds.gay, all paths were analysed. At first glance, it is noticeable that most paths end with a number consisting of one to three digits. These numbers were removed for further analysis. Afterwards, the following pattern emerges for the most frequently used paths:
The different paths each redirect to different websites. The partial presence of “de” in the paths suggests that we are only seeing the German-speaking part of the spam wave here. It is also interesting to see that the different paths seem to change from one day to the next. This becomes even clearer if we look at the distribution over a period of two weeks:
It should also be mentioned that exactly these paths can also be recognised under other domains. This supports the assumption that all these spam URLs belong to a common cluster.
32Guards: Protection against Workday-Spam
Through the findings described in part here, 32Guards is now able to detect Workday-spam quickly and reliably.
In this blog article, we introduced you to the pattern of Workday-spam. Spam URLs distributed according to this pattern have been spotted in large numbers by 32Guards in recent months. The analysis suggests that the spam waves are tailor-made for the DACH region.
This article also shows how networking many NoSpamProxy installations enables 32Guards to detect patterns that remain hidden from the individual client. With this information, 32Guards can then provide much more proactive and large-scale protection against spam emails. In the case described here, 32Guards’ focus on the DACH region also proves to be a great advantage. Thus, patterns can be detected that might be lost in globally collected data sets.
Do you want to protect yourself from spam and do not yet use NoSpamProxy?
32Guards is available free of charge as an add-on in the current NoSpamProxy version. If the use of 32Guards is activated, no further configuration is necessary to benefit from the protection provided by 32Guards.