What is Authenticated Received Chain (ARC)?
Simply put, all sender reputation techniques are based on settings on the email system that, when configured appropriately, provide something like a public checklist for the legitimacy, authenticity, and integrity of emails from that domain.
ARC is the latest technology in sender reputation, and the RFC is in Experimental status as of July 2019. Its penetration rate is high, especially among cloud-based services such as Google and Microsoft, because as an authentication system it solves a known problem when using the other methods for sender reputation.
SPF, DKIM and DMARC work even better with ARC
Sender reputation checking allows the receiving server of an email to unambiguously determine whether the delivering server is authorized to deliver email on behalf of the sending domain (SPF) and whether the email is authentic and has remained unchanged in transit (DKIM). DMARC is technically based on these two procedures and defines how the recipient should authenticate and what should happen in the event of a failed check. Specifically, emails can be rejected, quarantined or allowed through.
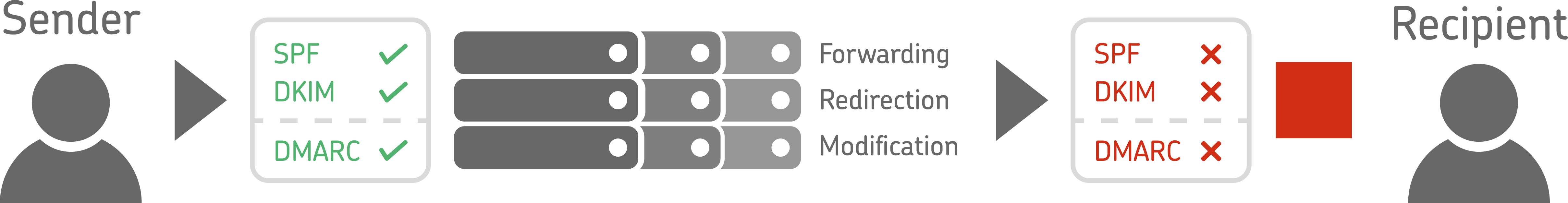
The problem: If DMARC is configured to reject emails, this may also affect legitimate emails under certain circumstances. This is the case, for example, if the email was forwarded or sent via a mailing list. Both scenarios then lead to errors in the SPF check because the forwarding server is usually not listed in the SPF entry of the original sender domain.
Also problematic can be changing the email subject or attaching email disclaimers or signatures, because this creates the possibility that DKIM validation will fail: The original email has been changed, after all.
The control chain reduces the error rate
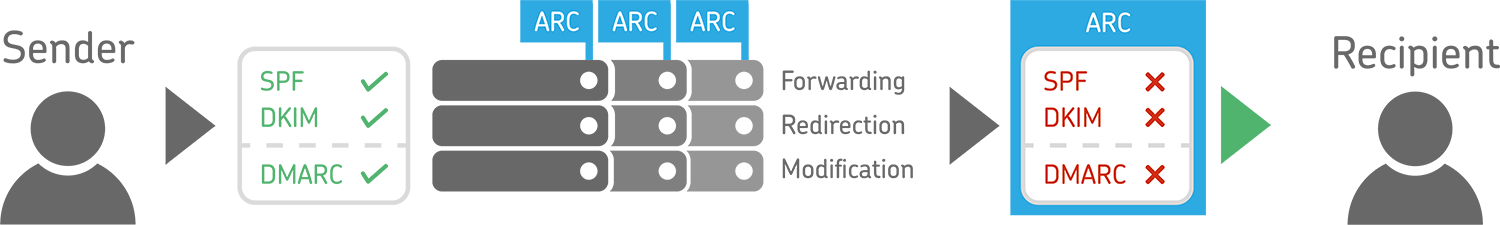
ARC now makes it possible to sign the original authentication results of an email. This allows a receiving service (server) to validate an email when the email’s SPF and DKIM entries become invalid due to processing by an intermediate server.
ARC thus preserves the results of the email authentication performed by SPF, DKIM and DMARC of all servers involved. (Intentional) modifications of the email thus no longer lead to errors. Each intermediate station that verifies an email with regard to SPF, DKIM and DMARC and modifies the header of the email accordingly also signs its own results with an ARC seal.
If the email is sent to the next server via redirection or forwarding, this server must also verify all ARC information of the intermediate stations according to the RFC. This creates the so-called chain of custody.
The SPF and/or the DKIM check and thus also the DMARC validation fails
The ARC seal preserves the successful SPF and DKIM checks, the email is delivered
Use ARC now – with NoSpamProxy Cloud
ARC provides the recipient with information about the results of SPF, DKIM and DMARC checks performed by the first participant in the ARC chain, as well as a way to verify the data sent and the mediating (forwarding) servers.
The effectiveness of ARC here depends on which e-mail servers trust each other. ARC is therefore primarily a tool for making forwarding and redirection that no longer works via SPF, DKIM and DMARC operational again.
ARC’s penetration rate is still low, but with NoSpamProxy Cloud you can already benefit from ARC validation and thus from an even more reliable sender reputation check.