Dynamic Data Exchange enables attacks
A feature for the dynamic data exchange (Dynamic Data Exchange or DDE for short) in Microsoft Excel, to which CSV files are usually linked, enables this approach. Microsoft released security enhancements as defense-in-depth measures for Excel in a January 2022 update. In previous updates, such as in 2018, controls were added to allow DDE to be configured in Excel. With the January update, Microsoft disabled DDE in all supported versions of Excel.
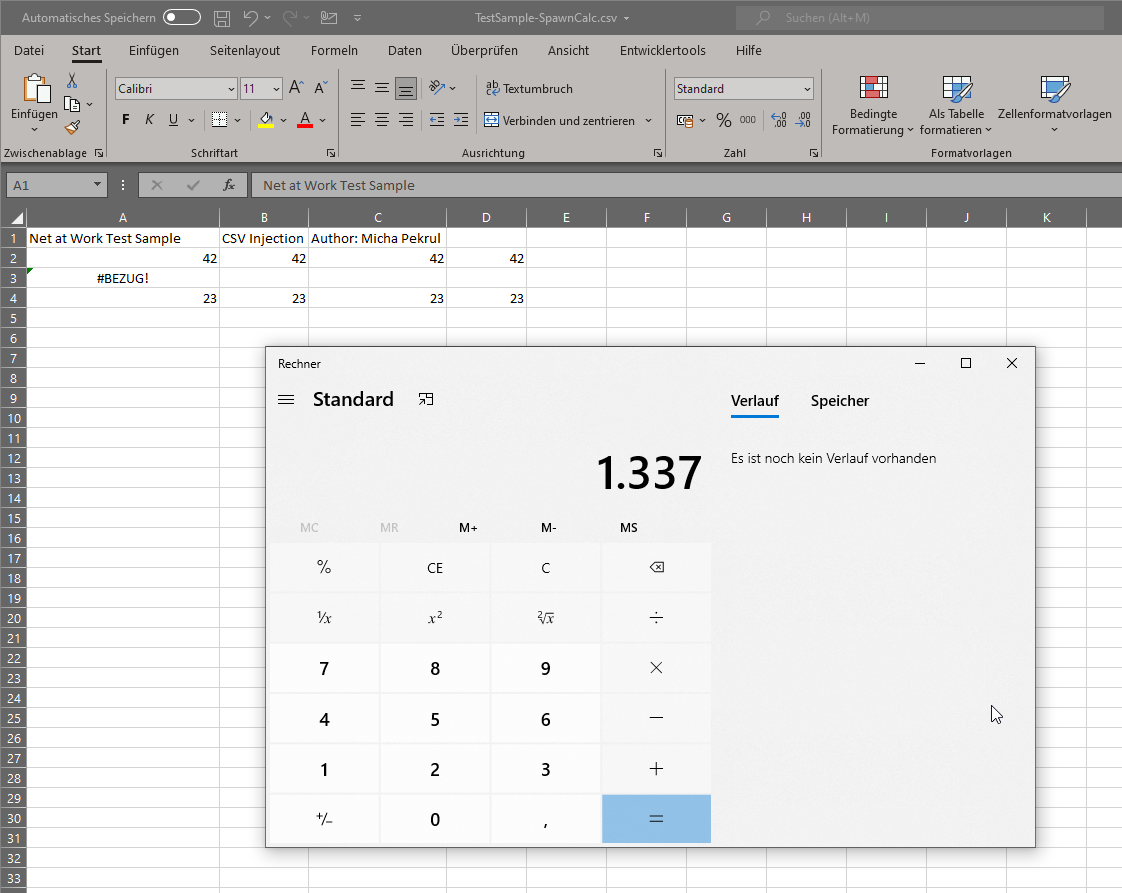
In order to get a CSV file in Microsoft Excel to start a program like “calc.exe” at all via DDE, you must re-enable the “DDE server start” option in the Trust Center on a fully patched system. As with documents with macro functionality, appropriate notes must be nodded off.
If you have not dealt with the issue of DDE in Microsoft Excel before, now is a good time to take a closer look at this potential threat. For most companies, it should certainly be enough to disable this often rather unknown functionality and roll out the new update.
How to protect yourself from CSV injection attacks with NoSpamProxy
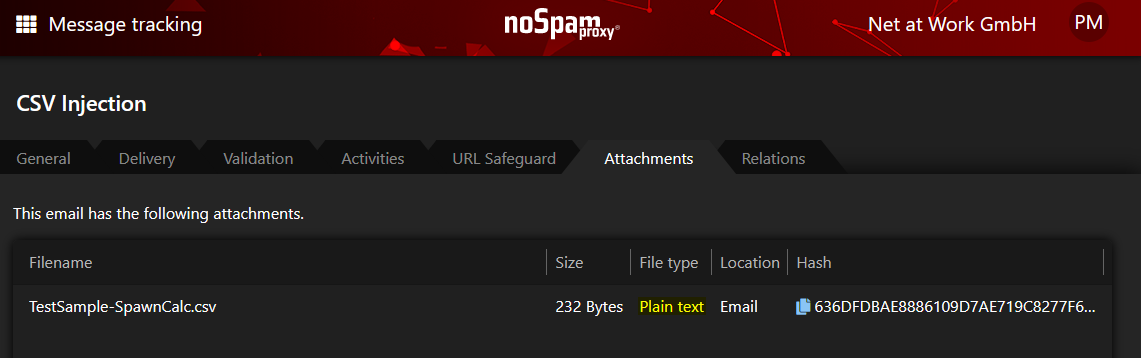
A CSV file is recognized in the NoSpamProxy file type “Plain text”.
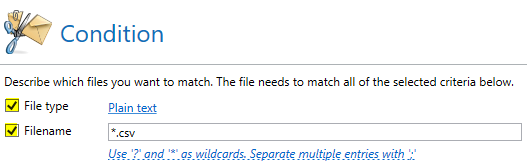
If such CSV files prepared with DDE functionality are sent as attachments via NoSpamProxy, they are correctly recognized as file type “Plain text”. So that you can filter them accordingly in the content filter, you must resort to an AND condition between file type “Plain text” and file name “*.csv”.
An AND condition filters on CSV files.
Now you can adjust the content filter according to your own needs. If CSV files are not needed at all in the company, you can reject the email completely. Or you can make a decision with the help of the level-of-trust filter. This distinguishes between trusted and untrusted communication partners. If you have licensed “Larges Files”, you can also separate a CSV file from the e-mail for security purposes, upload the attachment to the Web Portal and have it released there if required.
Basically, since the end of 2018, we propagate the so-called “email firewall“. We recommend to prohibit all files and only selectively – as with a firewall – allow individual required formats. So if in doubt, do not accept CSV files for the time being.
Not yet using NoSpamProxy?
With NoSpamProxy you reliably protect your company against cyber attacks. Request your free trial version now!